What are the different IAM protocols, when are they used and for what?
Cybersecurity Policies are integral for safeguarding an organization’s assets, reputation, and trust. It establishes a benchmark for measuring security-related activities, guides the best practices and roles, and underscores the importance of accountability. This policy framewprl envelops all assets (tangible, intangible, digital, and physical), entities (from employees to partners), and operations across diverse geographical locations. This is intended to serve as a guide for questions to be answered based on your areas of business or client focus.
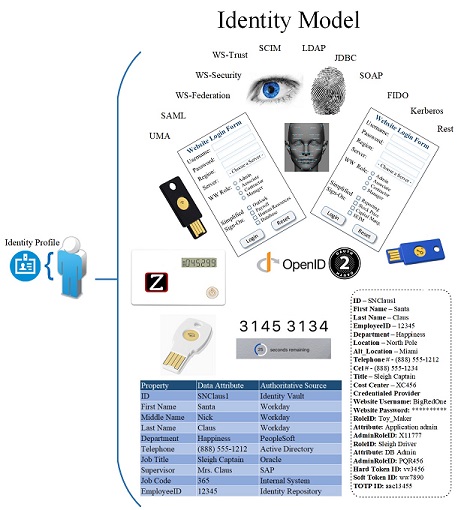
Here is a breakdown of the common protocols:
Monitoring & Auditing stand as cornerstones in cybersecurity frameworks, ensuring an organization remains vigilant against both external threats and internal weaknesses. Effective monitoring provides real-time insight into network activities, while auditing acts as a systematic review of these activities to ensure adherence to established cybersecurity policies and standards. Here's a comprehensive breakdown:
Monitoring & Auditing:
1. Regular Assessments:
Regular assessments maintain the organization's cybersecurity posture by actively checking for vulnerabilities and ensuring the continual application of security measures.
a. Vulnerability Scans:
Routine scans of systems and networks using automated tools to detect known vulnerabilities, outdated software, or misconfigurations.
b. Penetration Testing:
Simulated cyberattacks on the organization’s systems to identify weaknesses in its defenses. These can be both external (targeting public-facing systems) or internal (simulating an insider attack).
c. Compliance Checks:
Ensuring the organization is adhering to any relevant industry regulations or standards, such as GDPR, HIPAA, or PCI-DSS.
d. Patch Management Review:
Verifying that all systems are updated with the latest security patches in a timely manner.
e. End-point Assessments:
Regularly checking end-user devices (like computers and smartphones) to ensure they’re secured and not compromised.
f. User Access Reviews:
Periodically reviewing user accounts to ensure no unauthorized access and that employees only have access to data and systems relevant to their role.
2. Logs:
Logs maintain records of various activities within the organization's systems and networks, proving instrumental for forensic analysis, anomaly detection, and compliance.
a. System Logs:
Detailed records from operating systems, capturing events like system startups/shutdowns, software installations, and system errors.
b. Application Logs:
Records of events within specific software applications, which might include transaction logs in databases or access logs in web servers.
c. Security Logs:
Logs specifically tailored to capture security-related events, such as failed login attempts or firewall breaches.
d. Network Traffic Logs:
Records of data packets moving in and out of the network, invaluable for detecting unauthorized data exfiltration or malicious incoming traffic.
e. Log Retention & Protection:
Policies detailing how long logs should be retained and ensuring they’re stored securely. This is critical as attackers might attempt to delete or modify logs to cover their tracks.
f. Log Analysis & Anomaly Detection:
Employing automated tools that sift through vast amounts of log data to detect unusual patterns or activities that might indicate a security breach.
g. Audit Trail Creation:
Establishing a coherent timeline from logs can be invaluable during forensic investigations, providing a chronological sequence of events leading up to, during, and after an incident.
h. Backup & Archival of Logs:
Ensuring logs are regularly backed up and archived to protect against data loss and to meet regulatory requirements for data retention.
In conclusion, Monitoring & Auditing work in tandem to offer both a real-time and retrospective lens into the organization’s cybersecurity landscape. While monitoring offers immediate visibility and alerting, auditing provides a structured review and validation mechanism. Together, they ensure a responsive and accountable cybersecurity environment.
