Securing Apache - Debian/Ubuntu
Step 3d - Create/Enable Security Headers - Mandatory Step!!!
Creating and Enabling Security Headers
Security Headers seems to be one of the most skipped steps in just about every configuration out there. We have listed the minimum security headers config that should be included in every instance of Apache. Security Headers (to work against sniffing and manipulating our own content) are a whole topic to itself on how to control the connection with clients. Not to mention, what we could possibly to do anyone using header manipulation to injection all sorts of fun. Apache module and header manipulation is truly an art form that seemingly very few people understand. This is where the majority of the security work and tweaking comes into play in order to stay ahead of the curve. There are so many lovely options for headers and how to use them.
We are using headers to deal with things like:
- Clickjacking Attack
- Only using secure Cookies
- Not allow for framing options outside of our domain (X-Frame-Options)
- Only allowing JavaScript, Applications, PHP, HTML, images, movies, etc. to be run from the same domain only
- X-XSS-Protection
- X-Content-Security-Policy
- Remove the ETag
- Remove the FileETag
- Remove server version advertising
- Not allow sniffing of our domain assets for downloading or uploading an executable file
- Setup Cache Control
- Enable and disable web platform features
- Control the value of the referrer header in the link away from your page
Header Syntax usage: Header [condition] add|append|echo|edit|edit*|merge|set|setifempty|unset|note
Header [[expr=]value [replacement] [early|env=[!]varname|expr=expression] <--When we desire to alter our headers behavior
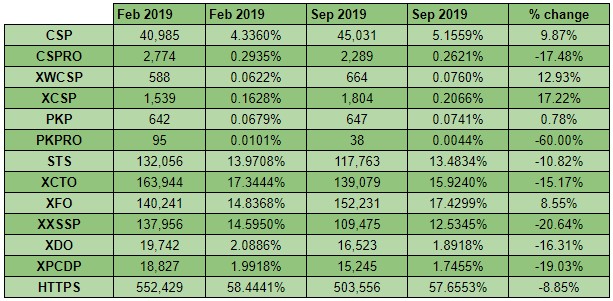
The below chart breaks down the top million requested websites - Scott Helme performed this very interesting study about the lack of Security Header use in the top million requested website's. The results for Februay 2019 came in. Whilst things didn't look too great in the first scan back in 2016, the rate of improvement being shown is incredible! These numbers are still a long way from where we'd like to see them but all of the metrics are showing considerable progress. Scott Helme Security Headers Test- securityheaders.io
We do not recommend using security headers as a global configuration and will not show an alternative way of using them.
Adding Headers to Apache Web site config file
nano /etc/apache2/sites-available/EXAMPLE_com_ssl.confAdd Security Headers <--Copy the sections in blue to the file
<IfModule mod_ssl.c>
<VirtualHost *:443>
..............................
<IfModule mod_headers.c>
Header unset ETag
Header set MyHeader "%D %t"
FileETag None
Header unset Server
Header always set X-Content-Type-Options "nosniff"
Header always set X-XSS-Protection "1; mode=block"
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
Header always set Referrer-Policy "no-referrer-when-downgrade"
Header set X-Frame-Options DENY
Header merge Cache-Control no-cache env=NO_CACHE
Header append Cache-Control s-maxage=600 "expr=%{REQUEST_STATUS} == 200"
Header set MyHeader "Feel safe zombiesecured headers in use!!! It took %D microseconds for Zombiesecured to serve this request on %t"
Header always set Permissions-Policy "accelerometer 'none'; camera 'none'; geolocation 'none'; gyroscope 'none'; magnetometer 'none'; microphone 'none'; payment 'none'; usb 'none' "
</IfModule></IfModule>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Close and exit the file
ctrl + o (Save)ctrl + x (Exit)
Restart Apache
systemctl restart apache2Zombie Security Headers Results
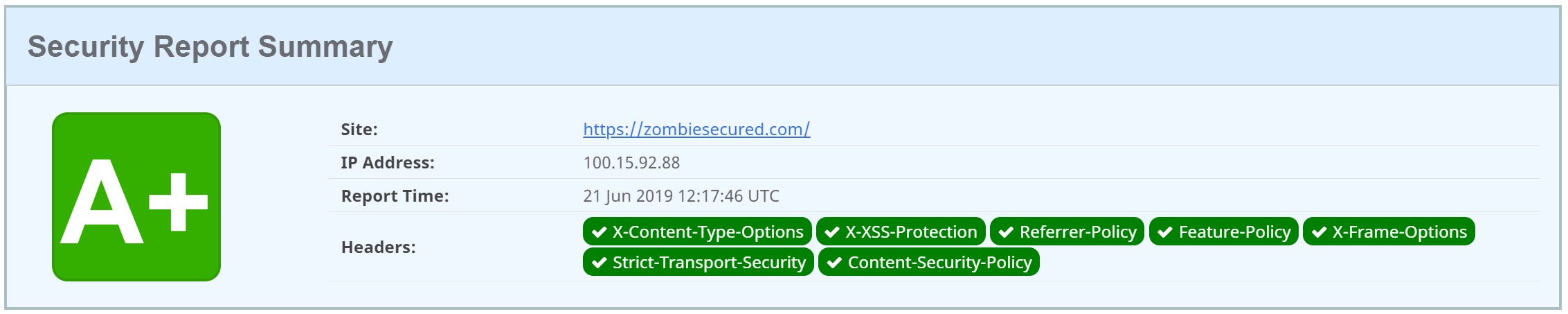
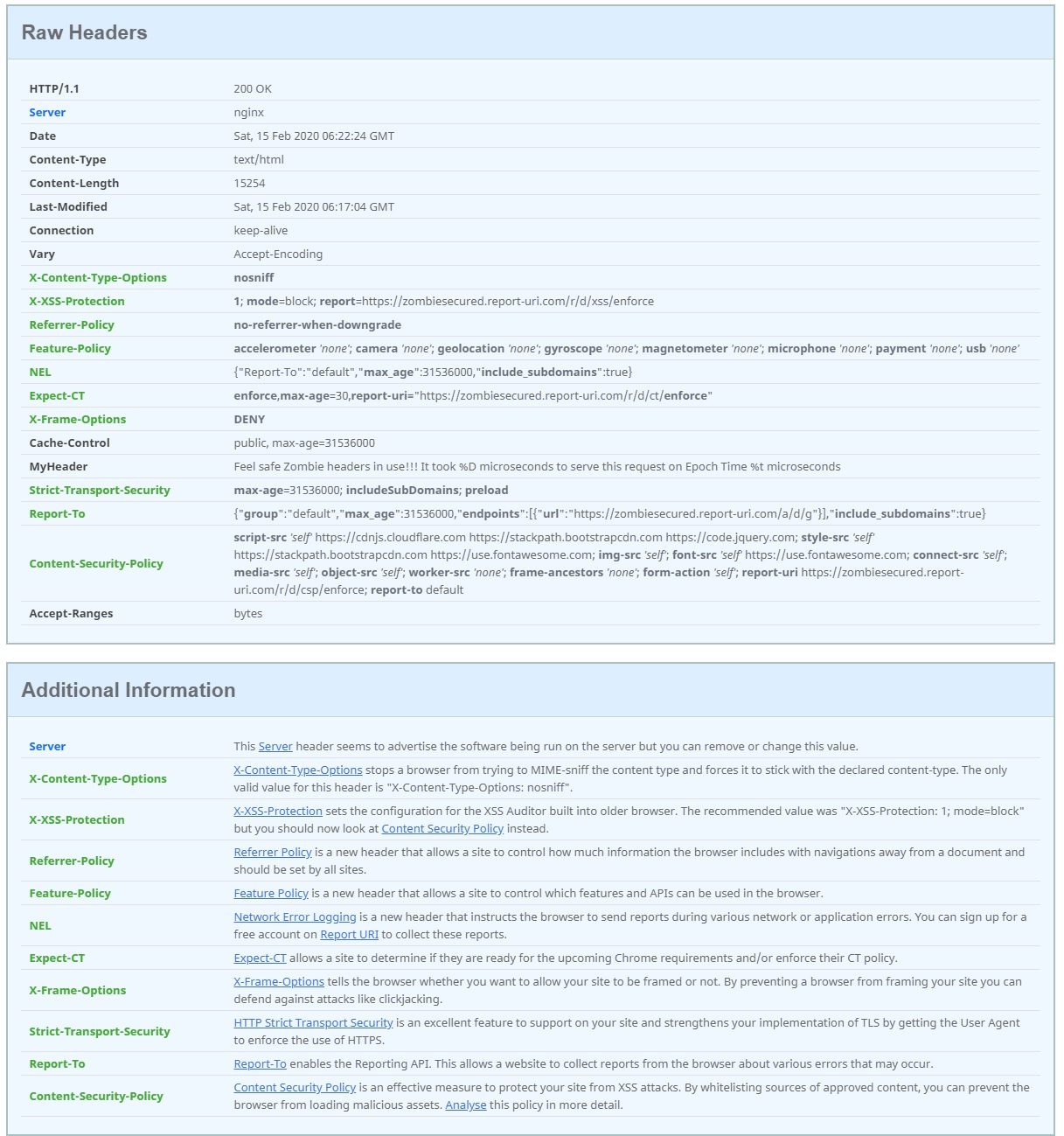
Test results June 20th, 2019 - Image courtesy of Securityheaders.io