Securing NGINX - Fedora/RedHat
Step 3f - Enabling Expect-CT - Highly Highly Recommended!!
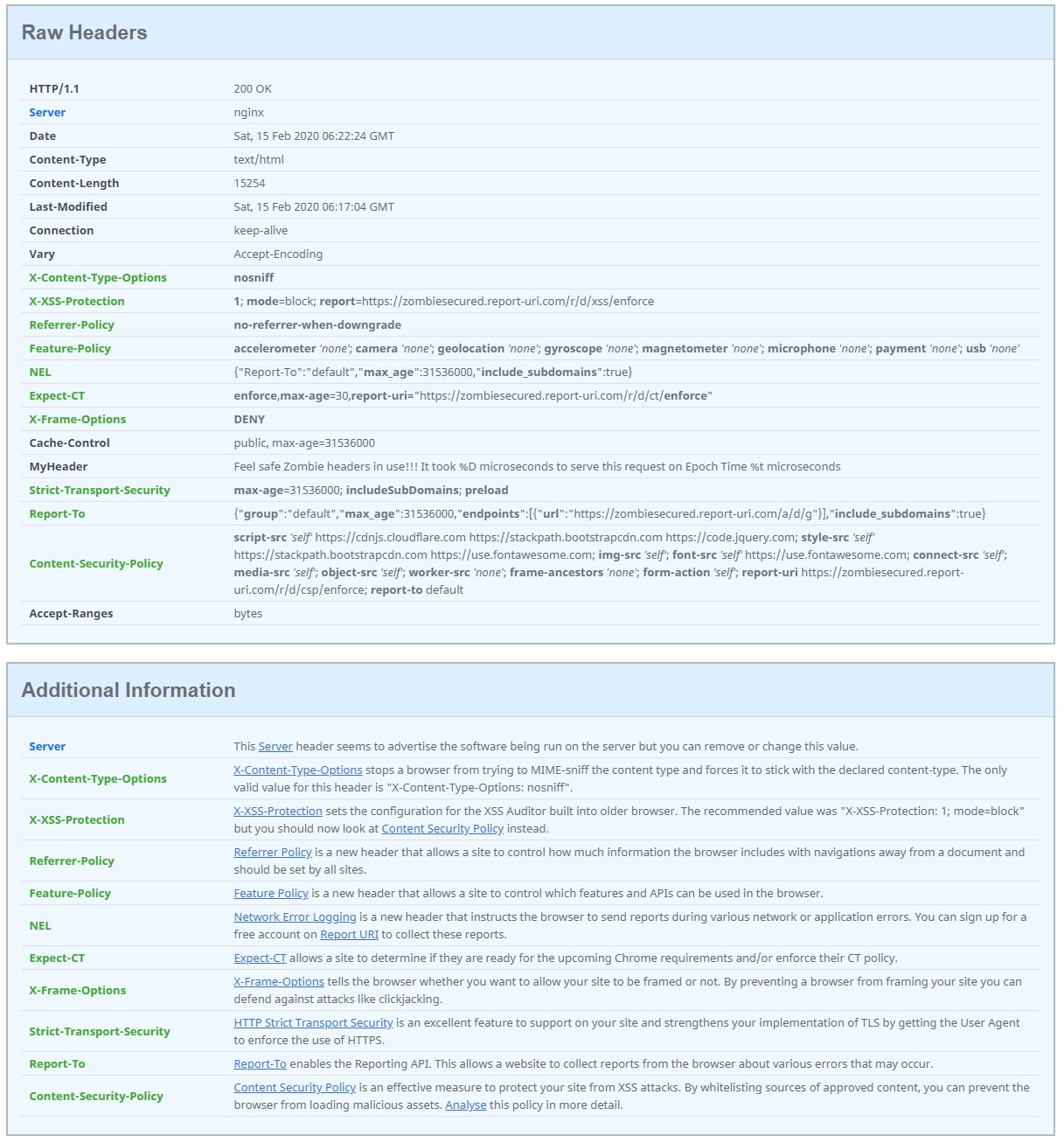
Enabling Expect-CT
Google's Certificate Transparency project fixes several structural flaws in the SSL certificate system, which is the main cryptographic system that underlies all HTTPS connections. These flaws weaken the reliability and effectiveness of encrypted Internet connections and can compromise critical TLS/SSL mechanisms, including domain validation, end-to-end encryption, and the chains of trust set up by certificate authorities. If left unchecked, these flaws can facilitate a wide range of security attacks, such as website spoofing, server impersonation, and man-in-the-middle attacks. You can find more info on their site.
Directives:
enforce
The optional enforce directive controls whether the browser should enforce the policy or treat it as report-only mode. The directive has no value so you simply include it or not depending on whether or not you want the browser to enforce the policy or just report on it.
max-age
The required max-age directive specifies the number of seconds that the browser should cache and apply the received policy for, whether enforced or report-only.
report-uri
The report-uri directive specifies where the browser should send reports if it does not receive valid CT information. This is specified as an absolute URI.
Change the HTTPS Web site config file <--Add the sections in blue to the file
nano /etc/nginx/sites-available/EXAMPLE_com_ssl.conf server {
..............................
etag off;
add_header X-Content-Type-Options nosniff always;
add_header X-XSS-Protection "1; mode=block; report=<uri>" always;
proxy_cookie_path / "/; HTTPOnly:Secure" always;
add_header Referrer-Policy no-referrer-when-downgrade always;
add_header Feature-Policy "accelerometer 'none'; camera 'none'; geolocation 'none'; gyroscope 'none'; magnetometer 'none'; microphone 'none'; payment 'none'; usb 'none'" always;
add_header NEL "{\"Report-To\":\"default\",\"max_age\":31536000,\"include_subdomains\":true}" always;
add_header X-Frame-Options DENY always;
add_header Cache-Control "public, max-age=31536000" always;
add_header MyHeader "Feel safe zombiesecured headers in use!!! It took %D microseconds for Zombiesecured to serve this request on %t";
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
add_header Expect-CT enforce, max-age=30, report-uri="url" always; <--- You can gradually increase the max-age once you are confident that it has been set up properly
}
Close and exit the file
ctrl + o (Save)ctrl + x (Exit)
Restart NGINX
systemctl restart nginxZombie Security Headers Results