Securing NGINX - Fedora/RedHat
NGINX Procedure Test Results
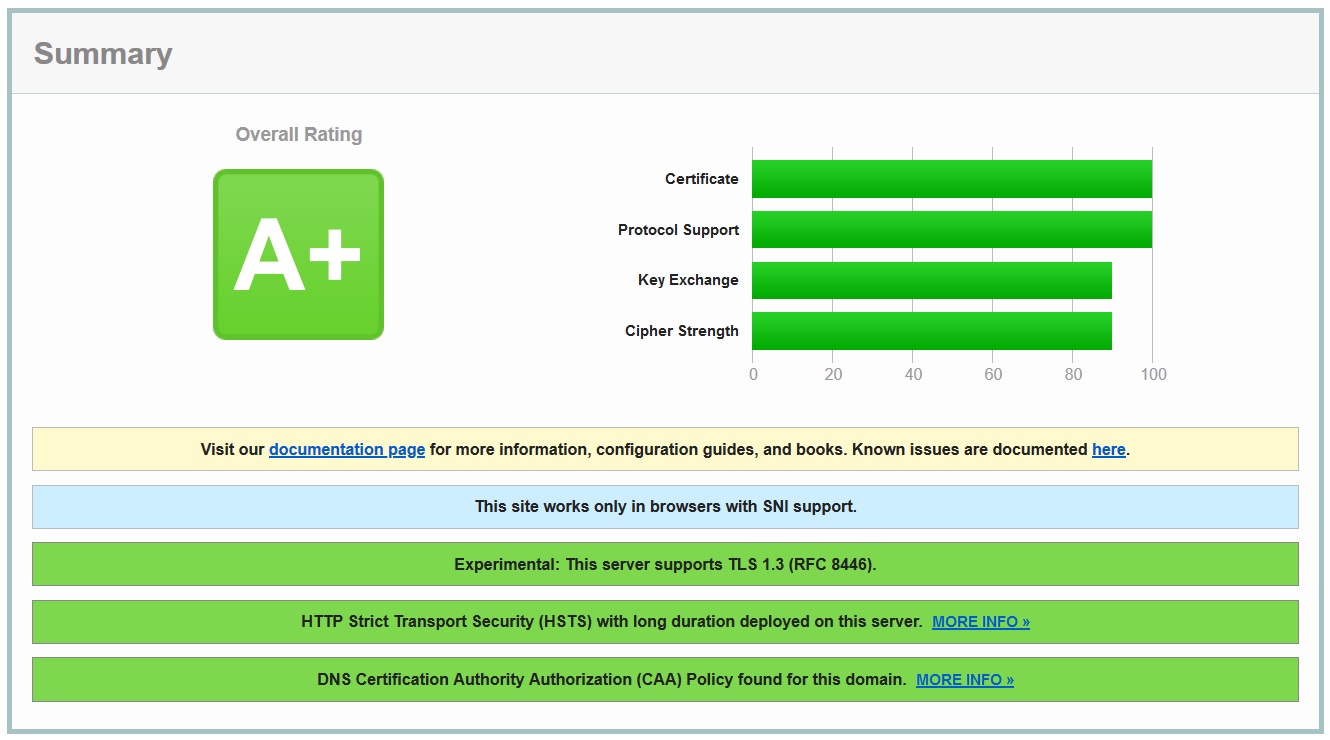
Summary of the test results
This is it!!! This is the result that we have been working on for everyone. Following this procedure will garner you an A+ in any pen testing application at very minimum cost. Before we rap up, there are some things that we need to go over and consider what these test mean. Please read the difference between the Modern, Intermediate and Old Security Configuration test results!
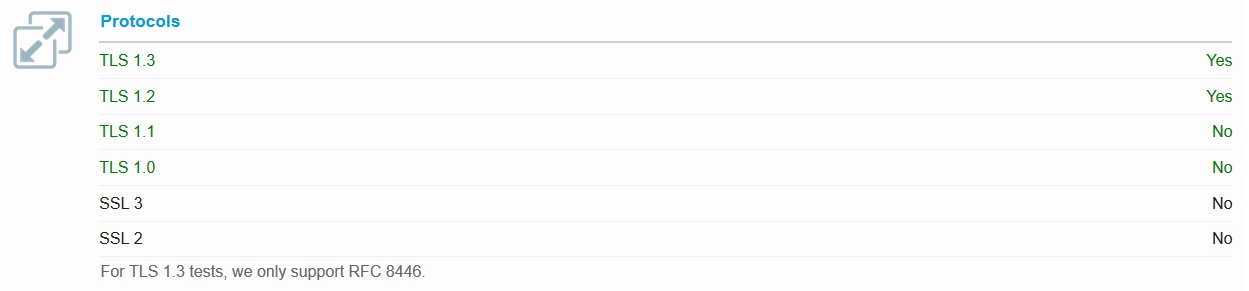
Protocols
Any protocol other an TLS v1.2 and TLS v1.3 is considered unsafe because it will give the attacker the ability to downgrade the secure connection to one of the insecure protocols and expose us to vulnerabilities. We at ZombieSecured are using TLS v1.3 as our first order of preference, then TLS v1.2 incase the broswer does not accept TLS v1.3 and dropped support for any other protocol to ensure maximum security.
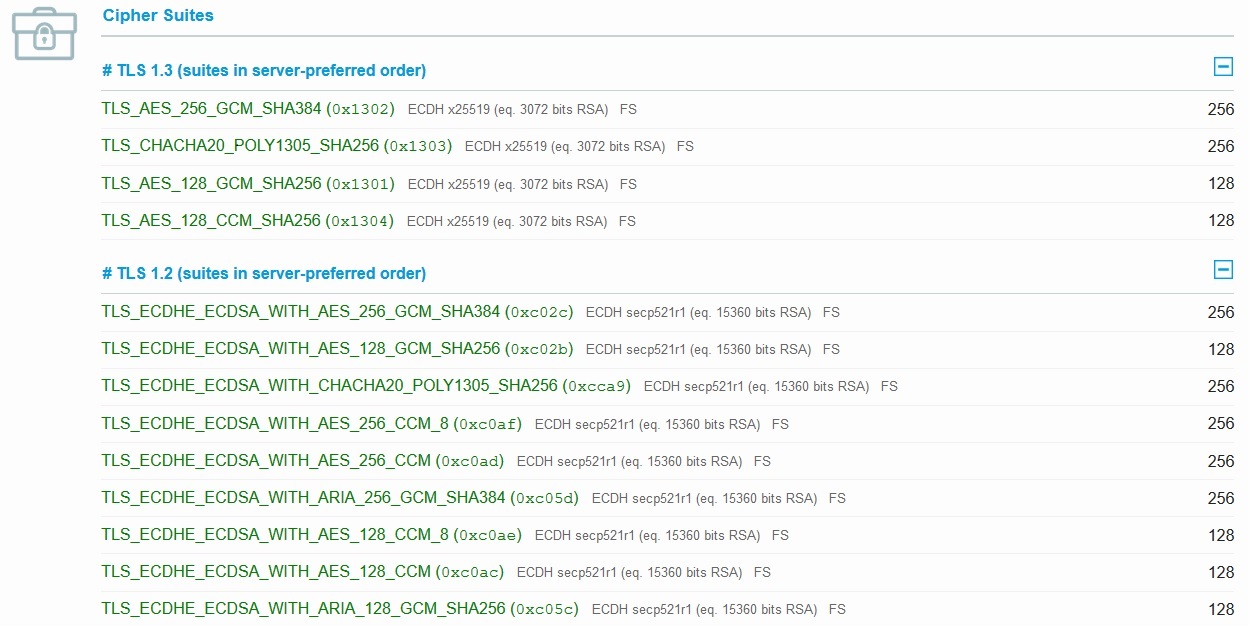
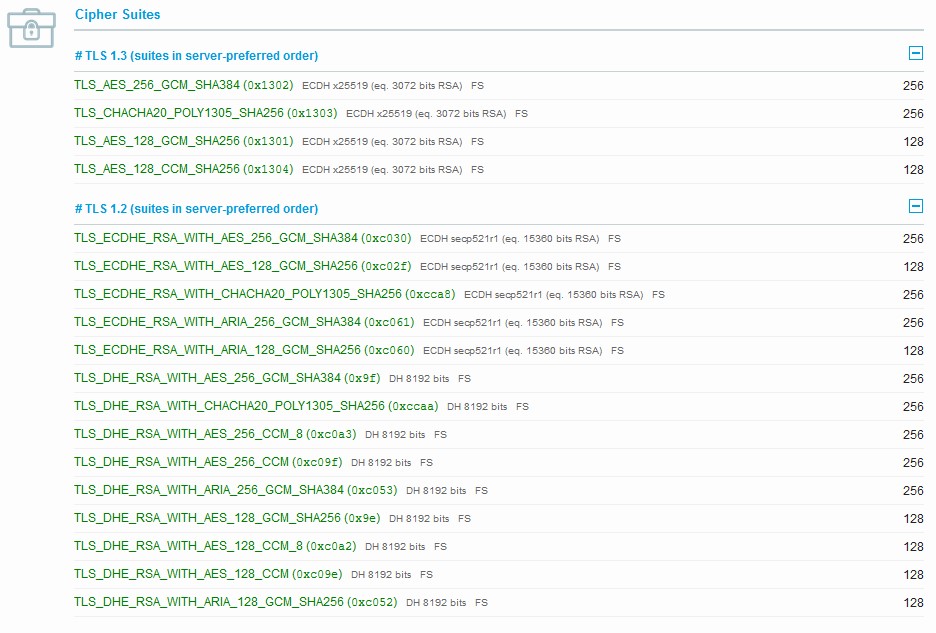
Modern Security Configuration
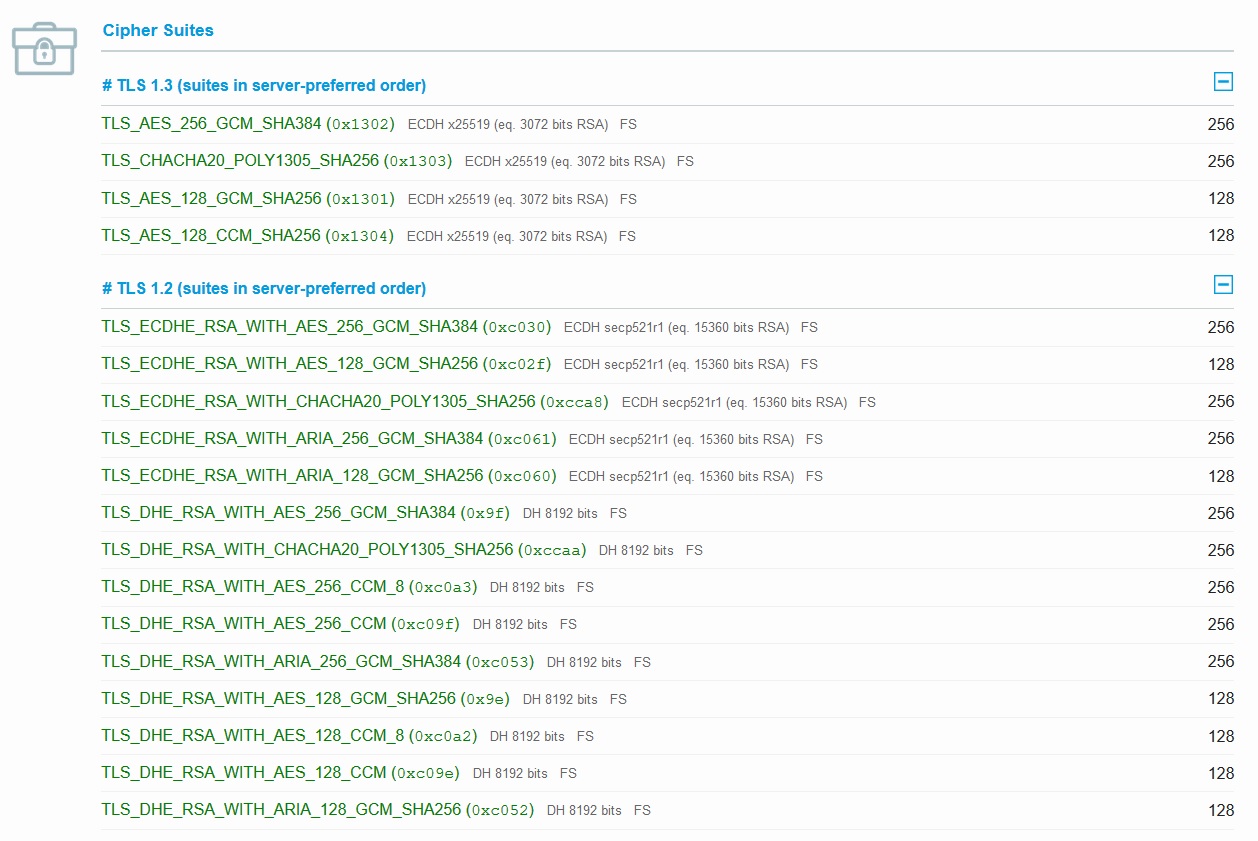
Cipher Suite
We should always make sure that we are communicating with the desired party and exchanging data securely. The ciphers that we choose in Step 3a will define how secure that communication takes place. You should always rely on a suite that provides strong authentication and key exchange. We have provided guideance throughout the site for what Cipher Suites should be used for NIST, HIPAA, PCI, SOX and so on. The Elliptic Curve Diffie-Hellmen key exchange used by Zombiesecured for TLS v1.3 is at least x25519 and the RSA key exchange is at 3072 bits as for TLS v1.2 the Elliptic Curve Diffie-Hellman key exchange is at least secp521r1 and the RSA key exchange is at least 15360 bits for ECC based Certificates.
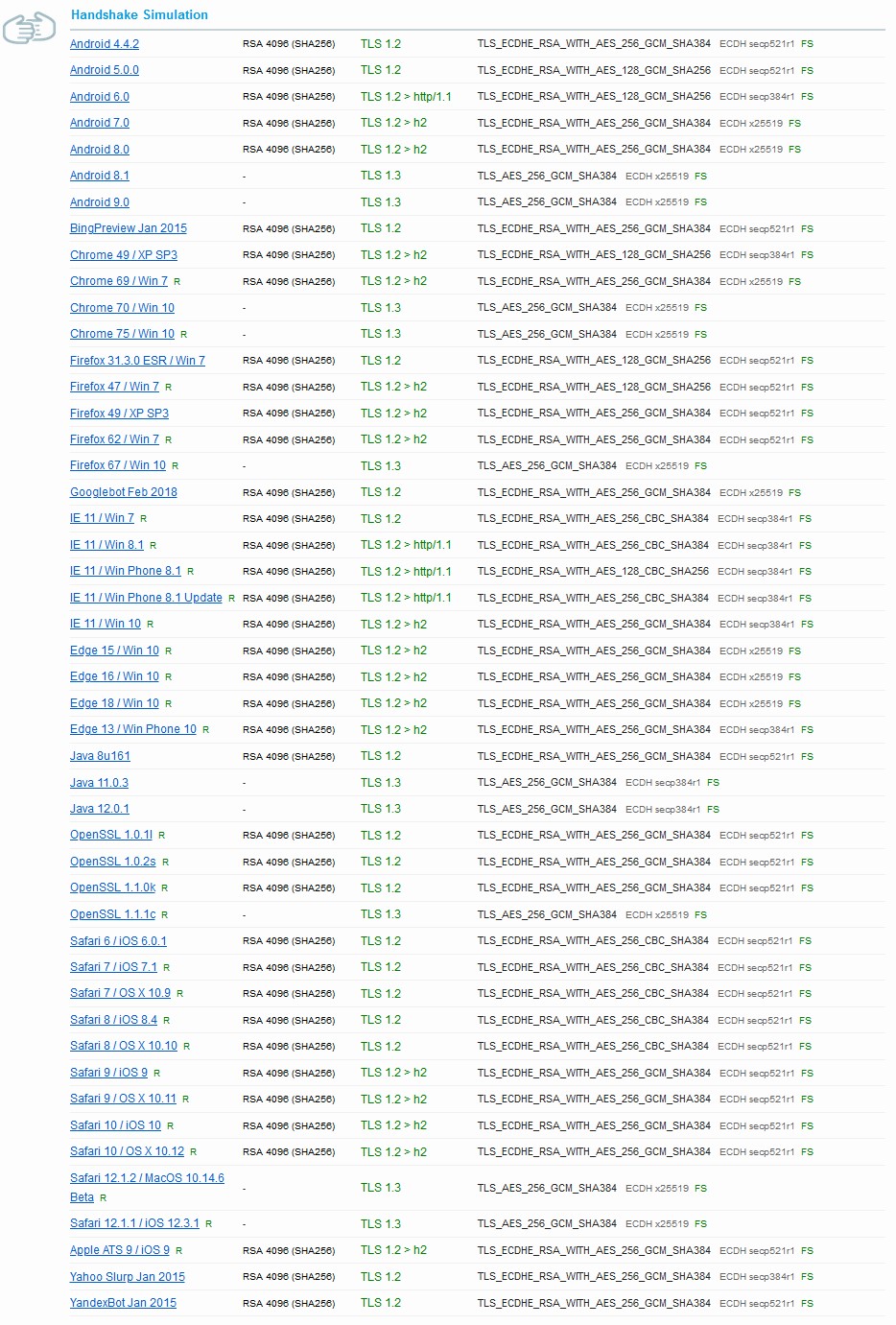
And the same goes for RSA based Certificates with support for additional Cipher Suites that support older browsers.
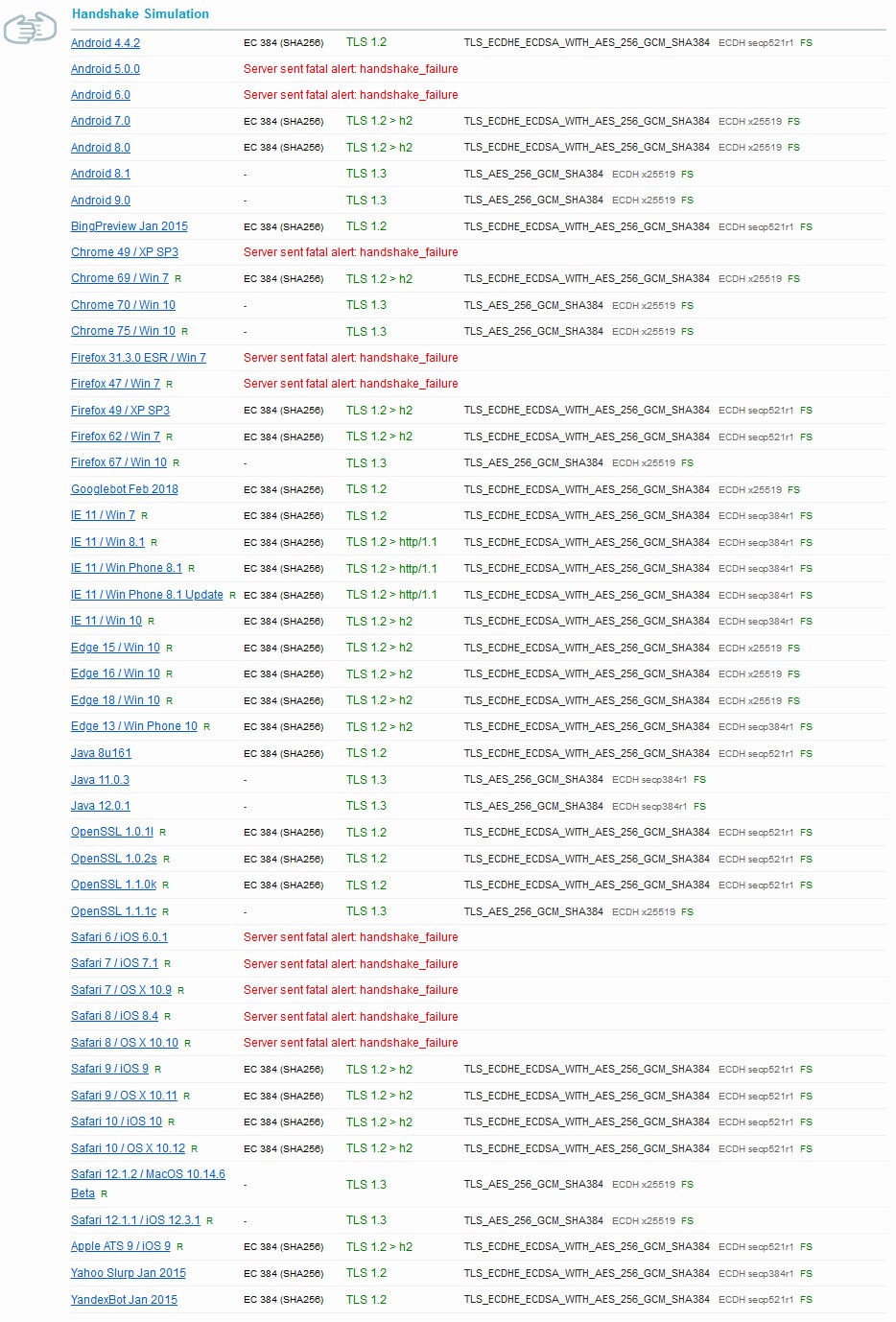
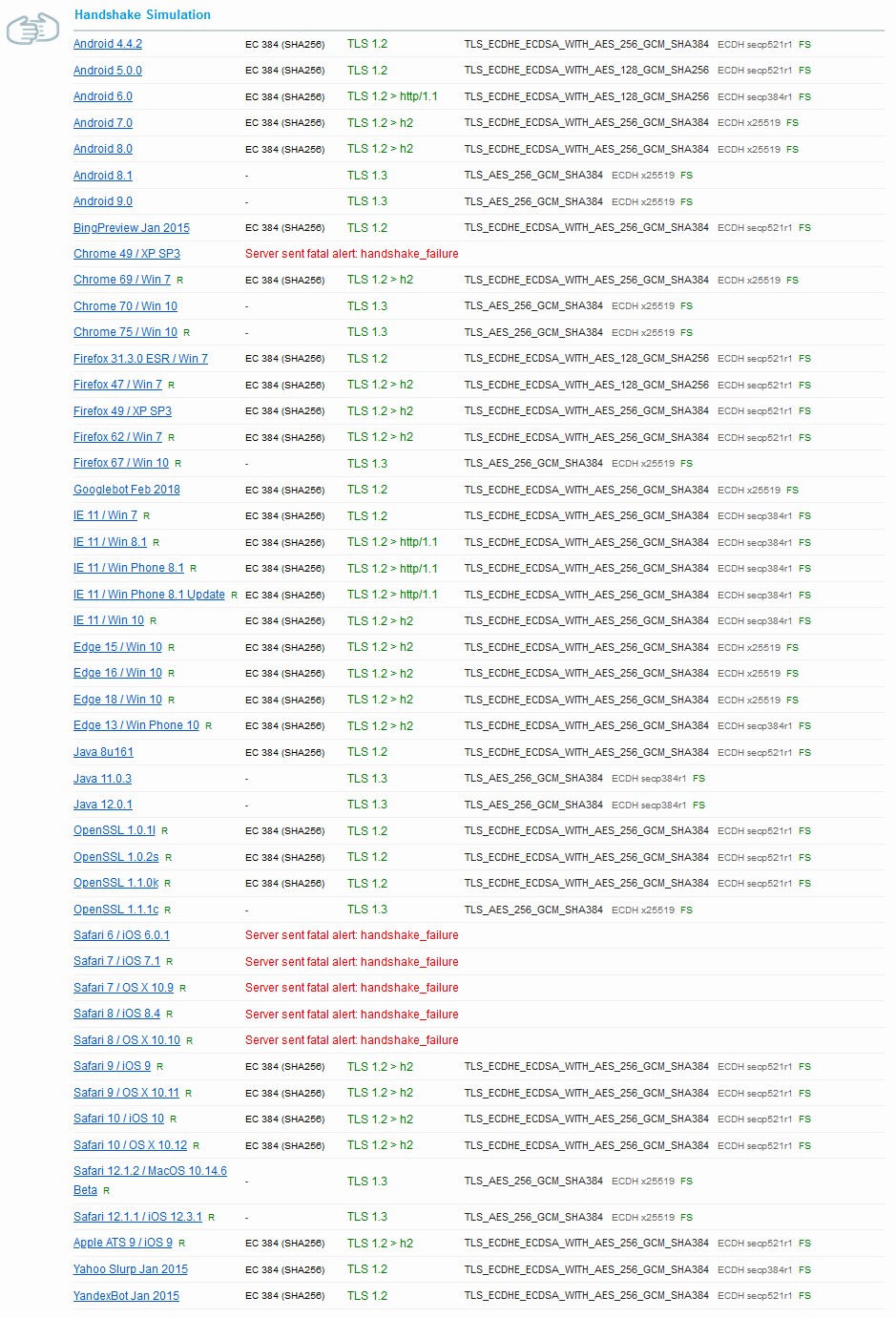
Browser support is important for deciding which Cipher Suites to use on the server. The Cipher Suite we recommended in this procedure is considered to be a modern and secure suite. This configuration will support modern clients as noted below for ECC based Certificates. Support for older browsers will be dropped because of their inability to support these secure settings. We will see the difference in broswer support in the following section based on the Cipher Suite that is in use.
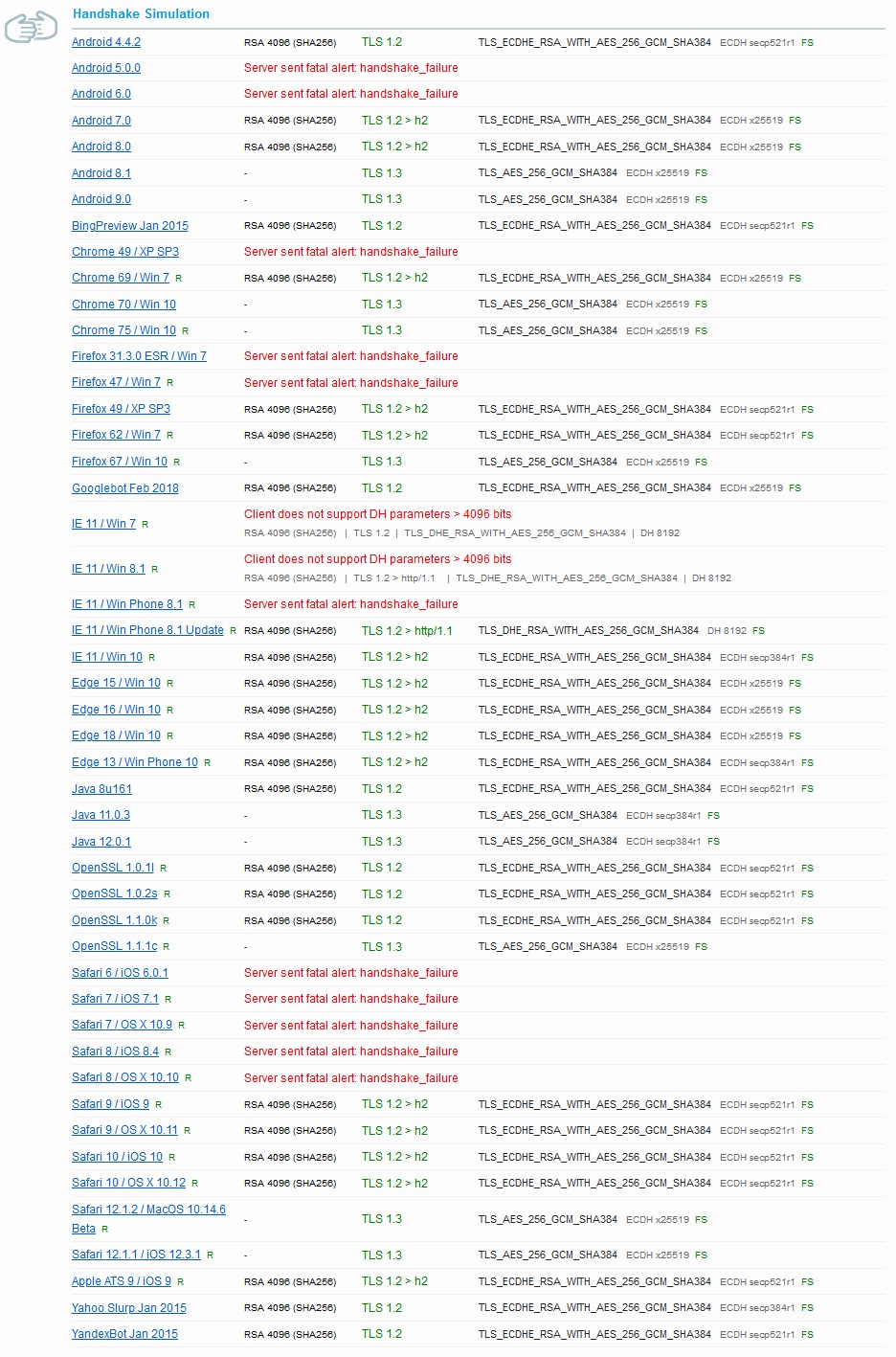
Below is an illustration for modern browser support for RSA based Certificates.
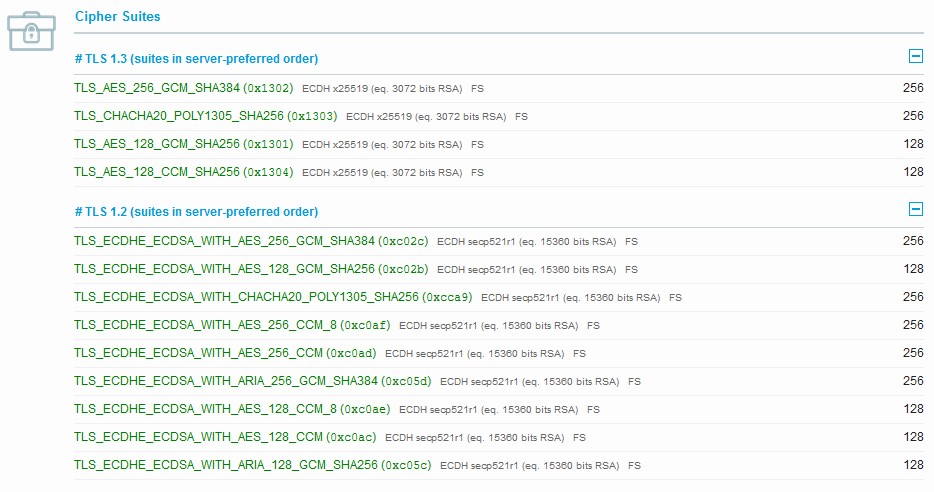
Intermediate Security Configuration
In some cases going with an Intermediate Cipher Suite will help in expanding the audience of the site as by covering more Ciphers as noted below for ECC based Certificates.
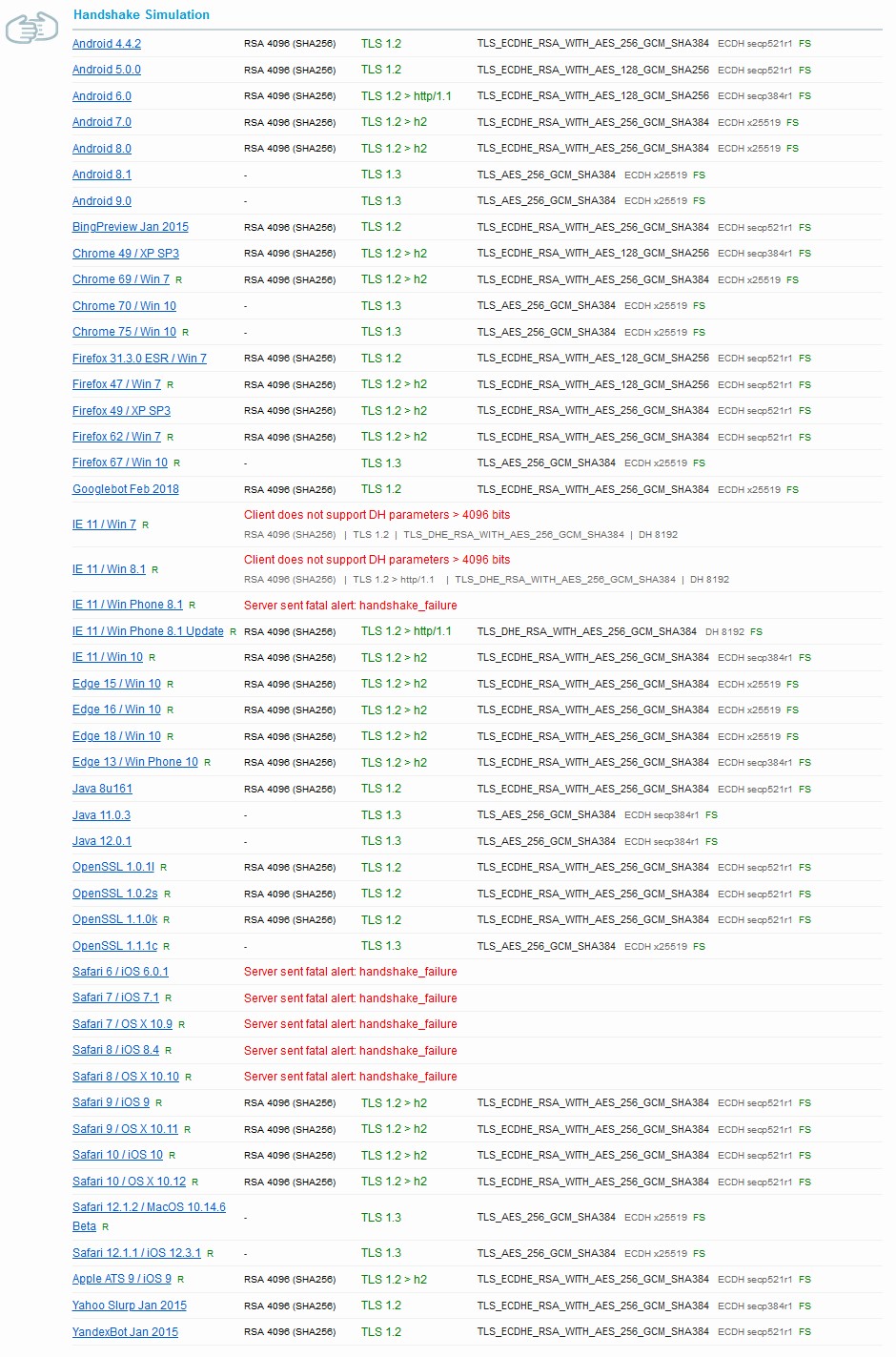
Below is an illustration for RSA based Certificates.
Going with such a suite will give you the ability to negotiate with not so older clients as noted below for ECC based Certificates.
And the same goes for RSA based Certificates.
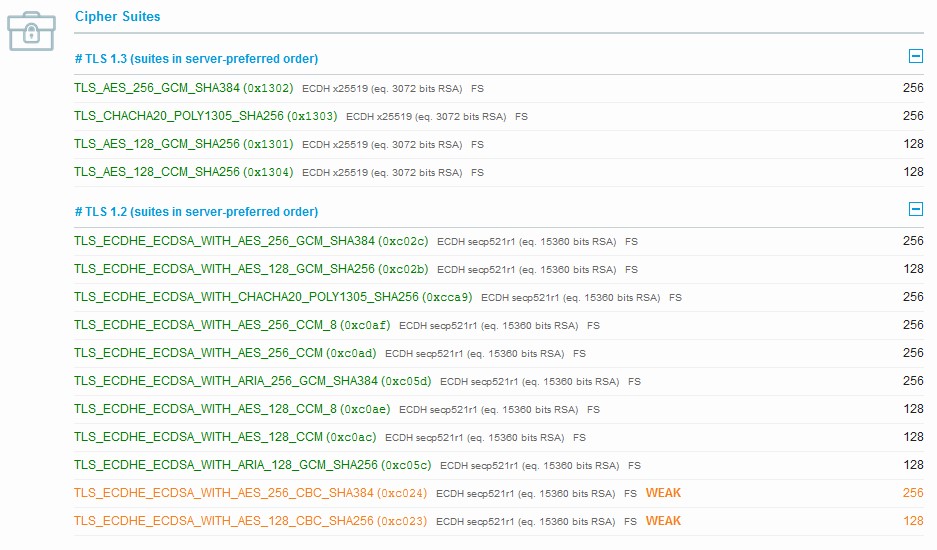
Old Security Configuration
In other cases going with an older Cipher Suite will help in expanding the audience of the site by covering legacy broswers. Using such cipher suite will result in having a combination of strong and weak ciphers as noted in the below image for ECC based certificates.
Below is an illustration for RSA based Certificates.
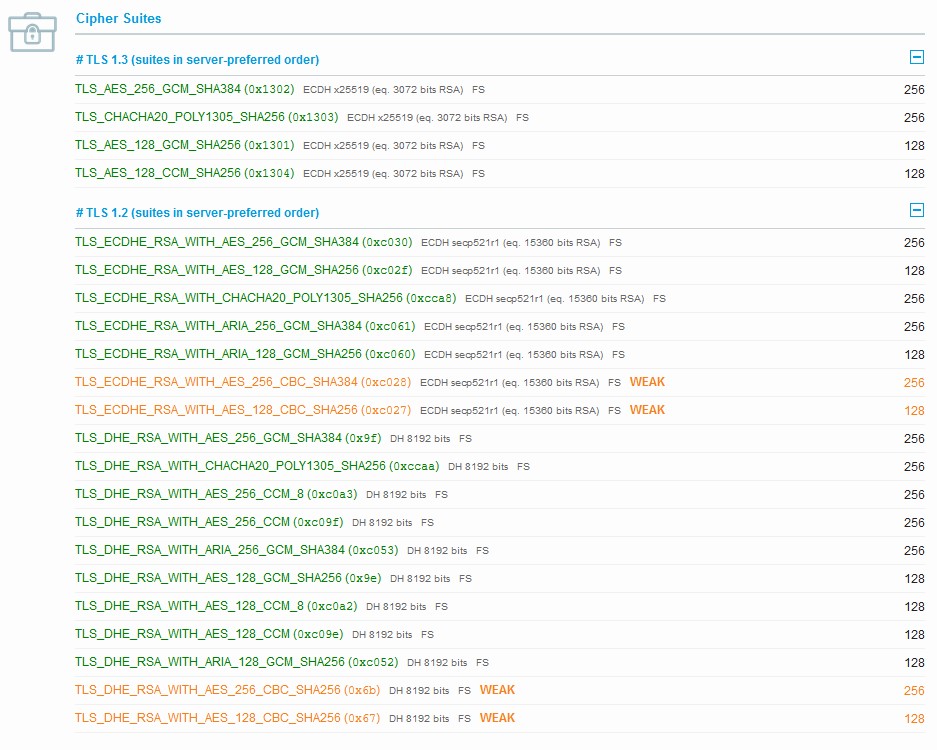
Going with such a suite will give you the ability to negotiate with older clients that don't support anyting better as illustrated in the image below for ECC based Certificates.
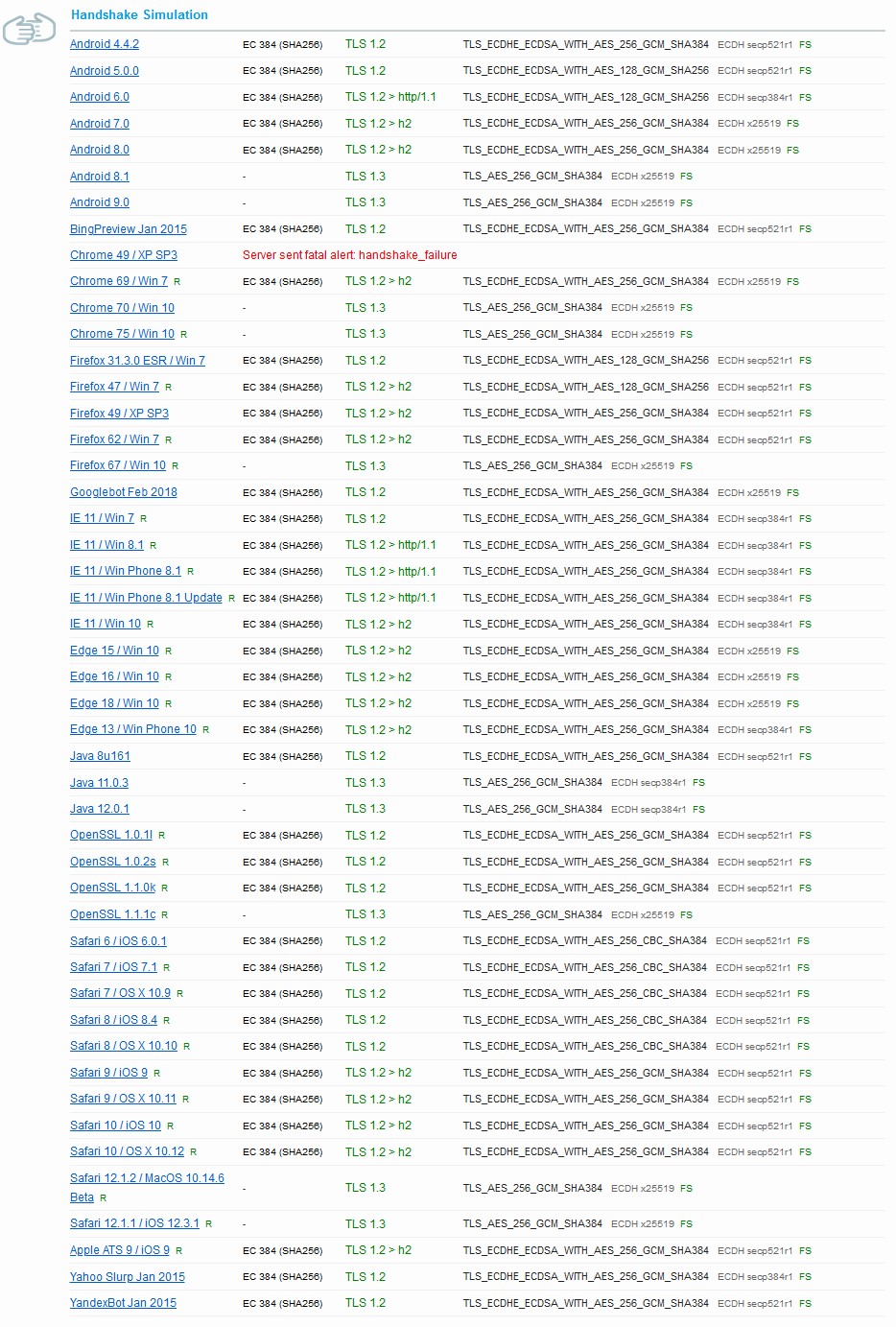
Below is an illustraton for the broswers supported by RSA based Certificates.