Multi-Factor Authentication (MFA)
What is Multi-Factor Authentication (MFA)? What are the Benefits and Goals?
Multi-Factor Authentication (MFA) is must for every organization!
Multi-Factor Authentication (MFA) is a powerful security mechanism that aims to verify a user's identity by requiring multiple authentication methods. While traditional authentication methods, such as a username and password, offer a single layer of security, MFA takes authentication to a higher level by incorporating additional verification measures. These supplementary methods ensure the authenticity of the user and can include various factors like smartphone-generated codes, security questions, fingerprint scans, facial recognition, hardware tokens, or biometric data.
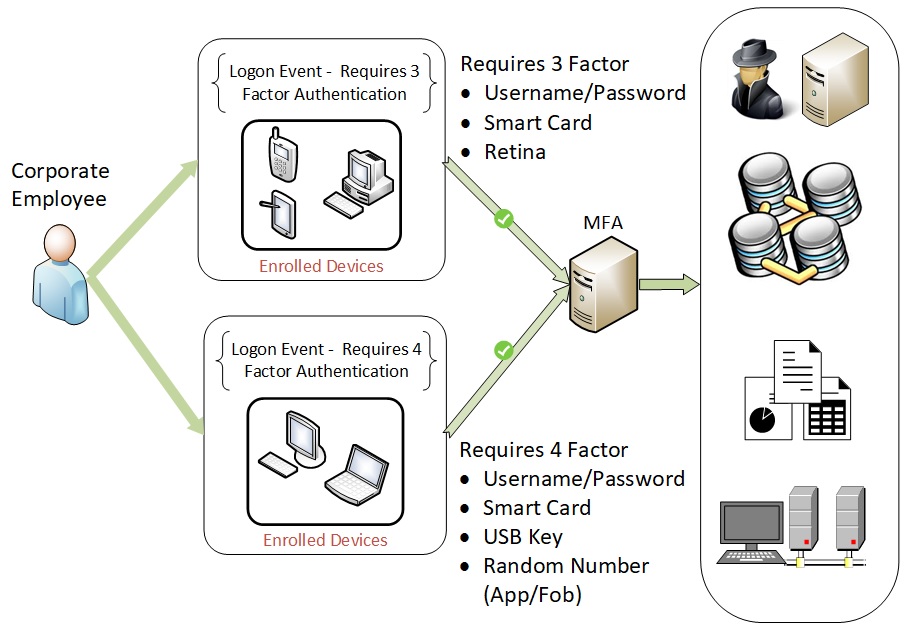
The implementation of MFA brings numerous benefits for organizations, making it a crucial aspect of their security strategy. Firstly, MFA enables compliance with relevant laws and regulations that apply to the business. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires organizations to implement strong access controls, including MFA, to protect sensitive cardholder data. Similarly, the Sarbanes-Oxley Act (SOX) mandates robust security measures to safeguard financial data integrity. By incorporating MFA, organizations demonstrate their commitment to meeting these compliance requirements and ensuring the security of sensitive information.
Furthermore, MFA helps organizations adhere to established standards and frameworks such as those defined by the National Institute of Standards and Technology (NIST), the International Organization for Standardization (ISO), and practices like ITIL and DevOps. These standards emphasize the importance of strong authentication practices and access control to mitigate security risks. By implementing MFA, organizations align with these standards, enhancing their overall security posture and demonstrating their commitment to industry best practices.
MFA can also be leveraged for controlling location-based access, particularly when integrated with Radio Frequency Identification (RFID) devices. This multifaceted approach to authentication allows organizations to implement higher security standards, especially when combined with login policies and location-based restrictions. For instance, by requiring employees to authenticate using their ID badges equipped with RFID technology, access to specific physical areas or rooms can be tightly controlled, ensuring that only authorized individuals can enter restricted zones.
In addition to strengthening security measures, MFA can lead to cost savings for organizations. By deploying MFA in conjunction with technologies like Geo-Fencing, wireless communication, Bluetooth, cellular networks, or Global Positioning Systems (GPS) within ID badges or RFID devices, organizations can automate access control processes and reduce the need for additional personnel to provide escort services. This not only streamlines operations but also minimizes costs associated with manual supervision and monitoring of access points.
Another advantage of MFA lies in its ability to facilitate the sharing of certain ID profile attributes with other systems or resources through header injection. This feature allows for streamlined integration and data exchange between various platforms, enhancing operational efficiency and improving user experience. By securely sharing relevant identity attributes, organizations can streamline user authentication and access processes, reducing the friction experienced by users when interacting with multiple systems.
MFA also supports step-up authentication, where additional authentication methods are triggered based on predefined policies. This provides organizations with flexibility in implementing security measures based on the level of risk associated with specific resources or transactions. For example, a financial institution may require customers to provide additional authentication factors when performing high-value transactions to ensure stronger security measures are in place.
Real-time analytics and reporting capabilities of MFA solutions provide valuable insights into access issues, allowing organizations to take prompt action and continuously improve their security measures. By monitoring authentication events, organizations can detect anomalies, identify potential security threats, and promptly respond to suspicious activities, thus enhancing the overall security posture.
The primary goals of implementing MFA are to instill utmost confidence in verifying the correct individual accessing enterprise resources. To achieve this, organizations establish policies that determine the appropriate number and types of authentication methods based on the access level and the sensitivity of the data being accessed. Additionally, MFA policies can take into account the access location and associated risks to determine the most suitable authentication methods for different scenarios.
To accomplish these goals, organizations can leverage software solutions that integrate with their existing identity stores and provide the desired authentication methods and geo-fencing capabilities. These solutions enable seamless integration with the organization's infrastructure and ensure a smooth user experience while maintaining robust security measures.
By implementing MFA, organizations benefit from heightened security, regulatory compliance, cost savings, improved access control, enhanced user confidence in verifying identities, and streamlined operations. Additionally, MFA supports the implementation of Bring Your Own Device (BYOD) policies, allowing users to securely access enterprise resources using their personal devices, further enhancing productivity and flexibility while maintaining security standards.