Identity Access Management
Identity Access & Lifecycle Management
Identity Access & Lifecycle Management with other considerations
This is a general illustration and does not account for numerous details.
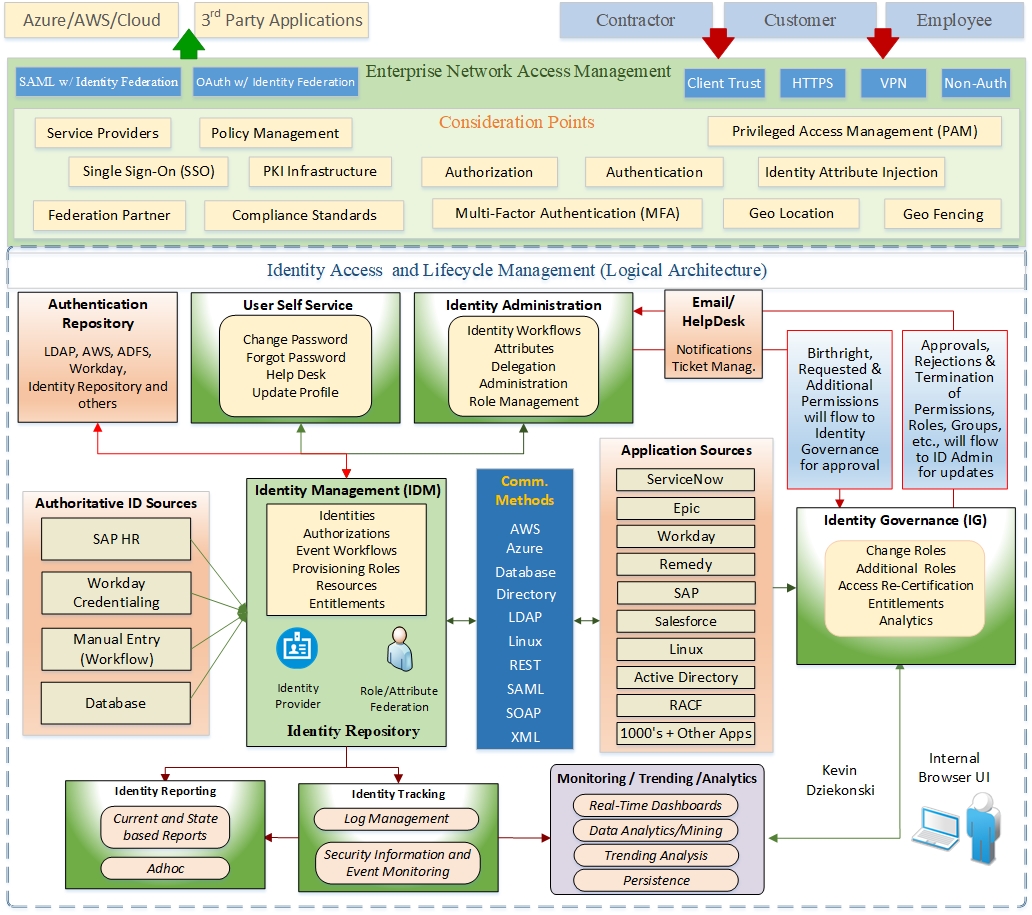
In the current digital age, protecting digital resources and confidential data is of utmost importance. Cybersecurity protocols serve as vital shields against cyber threats. However, an effective cybersecurity program is not merely an aggregation of individual components; it requires a holistic system that relies on the seamless interplay and coordination of various interconnected elements. One such critical component is Identity Access & Lifecycle Management (IAM), which encompasses network access management, identity governance and administration, authoritative sources for identity, policies, reporting, self-service capabilities, monitoring, analytics, and persistence.
Network Access Management serves as the gatekeeper of a computer network, responsible for managing user access to network resources. It establishes a secure environment by ensuring that only authorized individuals are granted appropriate access privileges. Robust access control mechanisms, such as multi-factor authentication and role-based access control, are employed to thwart unauthorized access attempts and mitigate the risk of potential security breaches.
Identity Governance and Administration plays a vital role in managing user identities, roles, and entitlements within an organization. It provides a framework for defining clear policies and procedures for identity management, ensuring that access privileges are granted in alignment with business needs and regulatory compliance requirements. Effective identity governance reduces the risk of insider threats, unauthorized access, and data leakage. It also streamlines user provisioning, deprovisioning, and access request management processes, making them more efficient and less error-prone.
Authoritative Sources for Identity serve as central repositories for user information and attributes. These sources act as the single source of truth for accurate and up-to-date user identity data. They may include HR systems, active directories, or identity management solutions. Integrating these authoritative sources ensures consistent and reliable management of user identities across the organization, enhancing the accuracy of access controls and minimizing risks related to identity mismanagement.
Multi-Factor Authentication (MFA) is a critical security measure that enhances user authentication by requiring multiple independent factors for validation. It adds an extra layer of security beyond usernames and passwords. Seamless integration of MFA throughout the network architecture strengthens authentication mechanisms, significantly mitigating the risk of credential theft and providing an additional barrier against unauthorized access.
A comprehensive Identity Access & Lifecycle Management system also considers factors such as self-service capabilities, monitoring tools, advanced analytics, and persistent security measures. Self-service capabilities empower users to manage certain aspects of their identity and access, reducing administrative burdens. Monitoring tools provide real-time visibility into access events and potential threats. Advanced analytics leverage machine learning and AI to predict and identify anomalies, while persistent security measures ensure that security controls remain effective over time. Together, these components work in unison to create a resilient and robust cybersecurity program capable of adapting to evolving threats and effectively protecting an organization's digital assets.
IAM also plays a crucial role in preventing identity theft, addressing insider threats, maintaining data integrity, and ensuring data confidentiality and privacy. By accurately identifying and authenticating users, IAM enables organizations to ensure that data is accessed, modified, or transmitted by authorized entities, while robust data integrity measures prevent unauthorized modifications or tampering. IAM solutions often include user monitoring capabilities and behavioral analytics to track user activities, detect suspicious patterns or anomalies, and prevent fraudulent activities. Data privacy measures, encryption, and access controls within IAM protect against unauthorized access, identity theft, and misuse of sensitive data. Compliance with regulations such as GDPR or PCI DSS further enhances fraud prevention efforts.
IAM can be integrated with advanced frameworks such as the Zero Trust model and Next-Generation Access Control (NGAC). The Zero Trust model challenges the traditional assumption of trust within a network environment by continuously verifying the identity and security posture of all users, devices, and applications attempting to access resources. NGAC introduces a flexible, attribute-based access control model that allows dynamic adjustment of access policies based on context, user attributes, and resource properties. These approaches enhance cybersecurity, strengthen identity protection, and minimize fraud risks by moving beyond role-based access control and continuously verifying the trustworthiness of entities.
Implementing IAM practices establishes a strong foundation for protecting identities and secrets. IAM frameworks enable robust user authentication, effective authorization and access control, confidentiality and data privacy safeguards, prevention of identity theft, mitigation of insider threats, and maintenance of data integrity. These measures are crucial for mitigating cyber risks, ensuring the trustworthiness of digital interactions, and establishing a resilient security posture in the face of evolving threats.