Java Keytool Introduction
Elliptical Curve Cartography (ECC) Certificate Signing Request (CSR) for a Certificate Authority (CA) w/ JCEKS Keystore
Generate a Certificate Signing Request (CSR) - ECC with JCEKS Keystore
The following example explains how to create a Certificate Signing Request (CSR) from a ECC JCEKS Keystore. The CSR will be forwarded to an Internal Certificate Authority (CA) or External CA (Thawte, DigiCert, Sectigo and so on) for verification. Keytool command options are listed at the bottom of the page.
The following breaks down the options we will use:
Create the CSR: -v (Verbose)
Name and location of file: site.csr
Signature Algorithm (sigalg): SHA224withECDSA / SHA256withECDSA / SHA384withECDSA / SHA512withECDSA
Signature Algorithm, Key Algorithm and is valid for 365 days (~1 years).
keytool -certreq -v -sigalg SHA512withECDSA -keyalg EC -validity 365
The password of the private key is "PWKey123" from the previous step. The key pair we created is stored in the keystore file this.keystore with format jceks.
-alias serverkey -keypass PWKey123
The keystore file name, the Keystore is of JCEKS type and password of the keystore is "changeit".
-keystore this.keystore -storetype jceks -storepass changeit
The first name is the Domain Name Service (DNS) will reference. The others listed maybe used for Subject Alternative Names (SAN)
-ext san=dns:server.example.com,dns:server,ip:10.10.10.10,ip:::1
Creating a Certificate Signing Request (CSR) from an ECC JCEKS keystore
Create the Certificate Signing Request (CSR)
Copy keytool -certreq -v -keyalg EC -file site.csr -sigalg SHA384withECDSA -alias serverkey -keypass changeit -keystore this.keystore -storetype jceks -storepass changeit -ext san=dns:server.example.com,dns:server,ip:10.10.10.10,ip:::1 Check the keys and keystore creation
Copy keytool -printcertreq -file site.csr 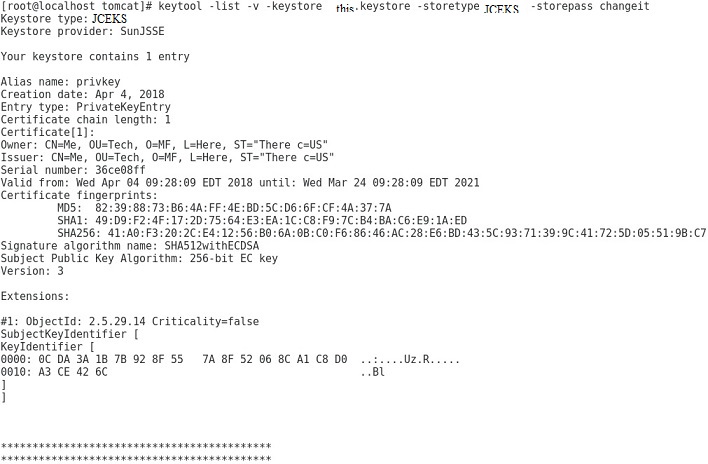
ECDSA based options
-sigalg SHA256withECDSA or SHA384withECDSA or SHA512withECDSA - Default is SHA256withECDSA Please use SHA256withECDSA or SHA384withECDSA or SHA512withECDSA
-keyalg Keysize ranges from 112 bits to 571 bits -Please use the default of 256 or preferred 384 or 521 (Most browers still support it despite being dropped from the NIST Suite B)