Privileged Access Management (PAM)
What is Privileged Access Management (PAM)? What are the Benefits and Goals?
Privileged Access Management (PAM)
What is it and what does it do?
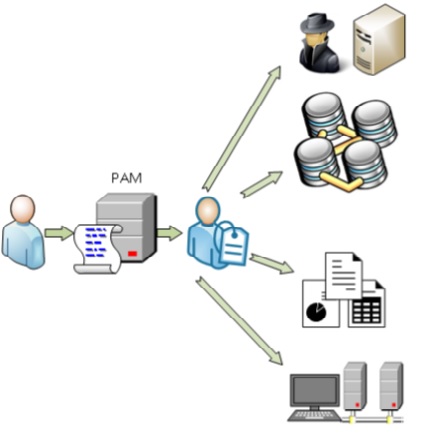
Privileged Access Management (PAM) helps to secure, control, manage and monitor privileged access to critical enterprise assets. This really means the root, administrators and people with access to sensitive data. PAM typically takes these sensitive credentials/privileged accounts and holds them inside a secure repository (Identity Vault). These accounts are now isolated, require check in/out and do not share privileged accounts passwords with the account user during the session. When the account is checked back in, the password is automatically reset.
Privileged Access Management by Gartner has the following subcategories:
- Shared access password manager (SAPM)
- Superuser password manager (SUPM)
- Privileged session manager (PSM)
- Application access password manager (AAPM)
By centralizing privileged credentials in one place, PAM systems can ensure a high level of security by handling real-time access requests, approval/disapproval workflow's, analytics, reporting, monitoring and suspicious activity policies.
Organizational Goals
- Comply with all applicable Laws and Regulations pursuant to the business
- Comply with all applicable Standards pursuant to the business
- Minimize access to resources only needed for Job Role
- Credential Check In/Out, One Time Password & Monitor/Record Privileged Accounts
- Higher security standards by using Multi-Factor Authentication based on log in policies and location
- Lower the cost and ease administration of systems
- Minimize the cost of user password resets/admin
- Analytics and reporting in real-time
Goals of Privileged Access Management (PAM)
- We want PAM to control and monitor high risk privileged accounts (HR, Payroll, Admin, Root)
- Check in/out credentials with session password not available to user
- Have a time limit on use of high risk privileged accounts
- Session termination for "rogue" commands not authorized to perform
- Have the password automatically changed after each use
- Provide ability to request/monitor real time access request to appropriate person for approve/disapproval
- Provide video/key board strokes recording of privilege account session
Accomplished by using software that integrates with the enterprise identity store(s) and the other enterprise resources desired to under PAM access control