Securing Apache - Fedora/CentOS/SUSE/RedHat
Step 3g - Content Security Policies (CSP) - Highly Highly Recommended!!
Content security policies are enacted by most of the larger content providers to minimize the amount of reloading of information. When if fact, it really is a great security measure to ensure that only our site is providing clients with content from our own sources and not someone else injecting code, malware and a vast array of other possibilities to perform against a site/server/client. It should be noted that less than one percent (1%) of the Internet has such policies and makes it easy to put my own source code in the middle of a communication stream. It is not mandatory since there are situations in which you do not wish to use CSP's at the server level. Unless you are an admin that understands those methods and implementations, use this procedure until you move the CSP to another area.
Scott Helme developed some nifty tools to help you generate a policy, analyses your policy or generate a hash of JS or CSS for your CSP
Change the HTTPS Web site config file <--Add the sections in blue to the file
nano /etc/httpd/conf.d/EXAMPLE_com_ssl.conf
<IfModule mod_ssl.c>
<VirtualHost *:443>
..............................
<IfModule mod_headers.c>
Header unset ETag
FileETag None
Header unset Server
Header always set X-Content-Type-Options "nosniff"
Header always set X-XSS-Protection "1; mode=block"
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
Header set X-Content-Security-Policy "allow 'self';"
Header set X-Frame-Options DENY
Header set Cache-Control:public, max-age=31536000
Header always set Strict-Transport-Security: "max-age=31536000; includeSubDomains; preload"
Header set MyHeader "Feel safe zombiesecured headers in use!!! It took %D microseconds for Zombiesecured to serve this request on %t"
Header set Public-Key-Pins "pin-sha256=\"Hash of Pin 1\"; pin-sha256=\"Hash of Pin 2\"; includeSubDomains; report-uri="https://report.EXAMPLE.com"; max-age=1111"
Header always set Content-Security-Policy: "" <--- Put your policy parameters between to the quotes - remove any redundancies
</IfModule>
</VirtualHost>
</IfModule>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Close and exit the file
ctrl + o (Save)ctrl + x (Exit)
Restart Apache
systemctl restart httpd
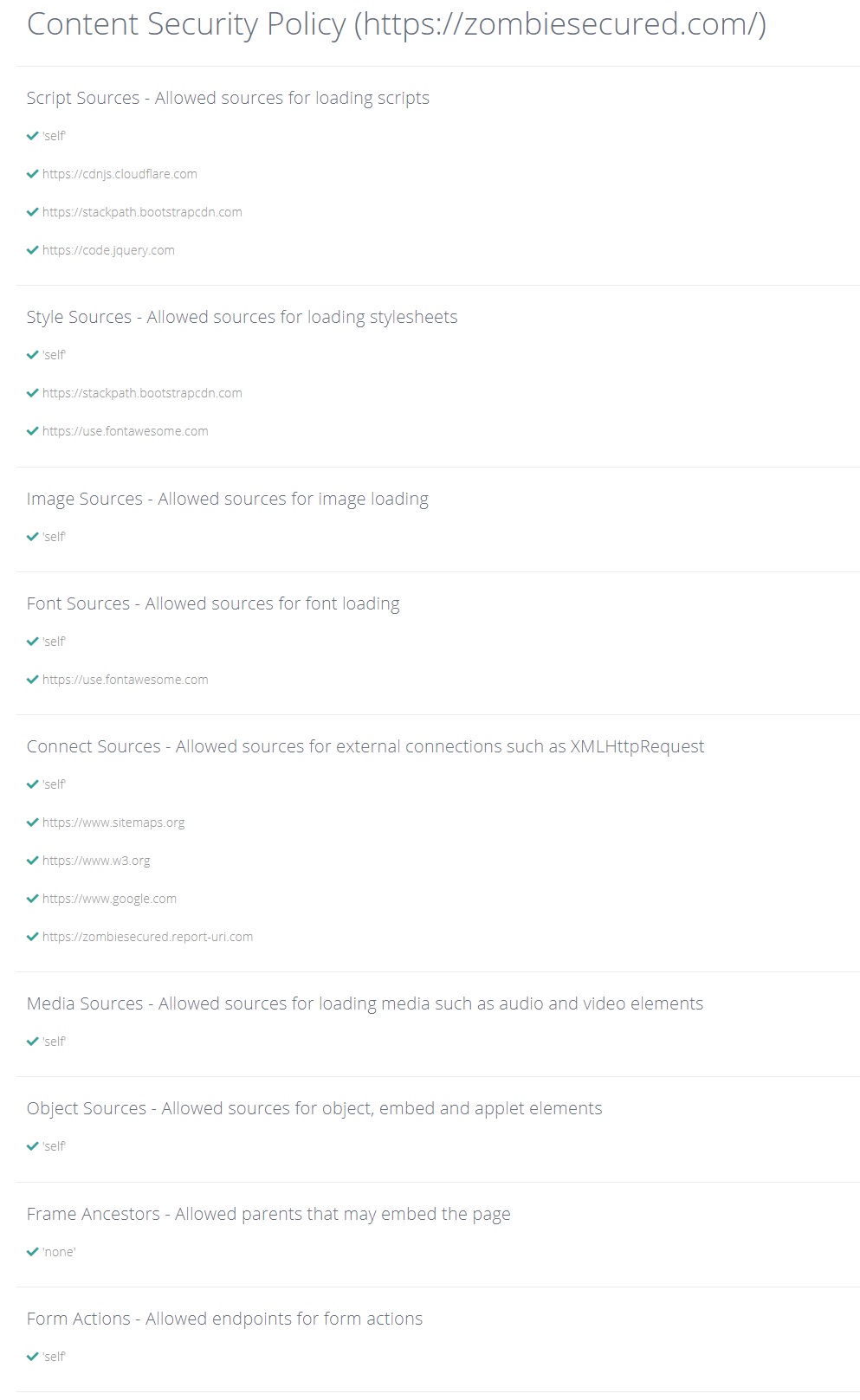
Zombie Secured Headers in use:
Header always set Content-Security-Policy: "script-src 'self' https://cdnjs.cloudflare.com https://stackpath.bootstrapcdn.com https://code.jquery.com; style-src 'self' https://stackpath.bootstrapcdn.com https://use.fontawesome.com; img-src 'self'; font-src 'self' https://use.fontawesome.com; connect-src 'self'; media-src 'self'; object-src 'self'; worker-src 'none'; frame-ancestors 'none'; form-action 'self'"
Zombie Secured CSP test results