Encryption Standards
Key and Curve encryption standards
Key and Curve Exchange Determination
Based on the tables on the prior page, you get the idea of what it takes to be secure. The recommended Zombie Apache and Tomcat configuration is good until 2167 minimum by any World standards!
If you are a government entity or corporation trying to protect intellectual property (IP), most likely this information will not be released to the public. These scenarios might require the highest security levels to protect state secrets or a corporations very existence. When conducting business on the internet, maybe having the highest standards could possibly limit your business. Having extermely high security standards could lose customers since they may not have the latest applications, browsers and so forth to take advantage of these strict standards.
The SSLLabs.com test will provide ratings based on the Keys strength as noted below. Our certificate will be using a 4096 bit key with the Elliptical Curve Diffie-Hellman (DH) ECDH secp256r1 (eq. 3072 bit modulus). Even though our key and certificate request will be generated with the use of secp384r1 and sha384, the Certificate Authority (CA) uses a 256 bit key to sign our certificate.
If we do not generate DH Parameters (2048 default in Apache) and update our our configuration, OpenSSL and Apache2 will not take advantage of the newly created DH Parameters benefits. Not to mention, we will not achieve a 100% in this area on the test.
To gain 100 percent on key exchange test, without limiting clients or overloading systems; we have to rethink how Apache2 connects to clients. Changing the way Apache2 negotiates connections with encryption we want, in order to achieve a RSA modulus equivalent to 15360 bit using DH Parameters. We will need to generate stronger DH Parameters in order to achieve this goal. If this configuration needs to be changed due to the Committee on National Security Systems announcement of changing standards, I will update this procedure as necessary.
Which type of encryption is for me and why?
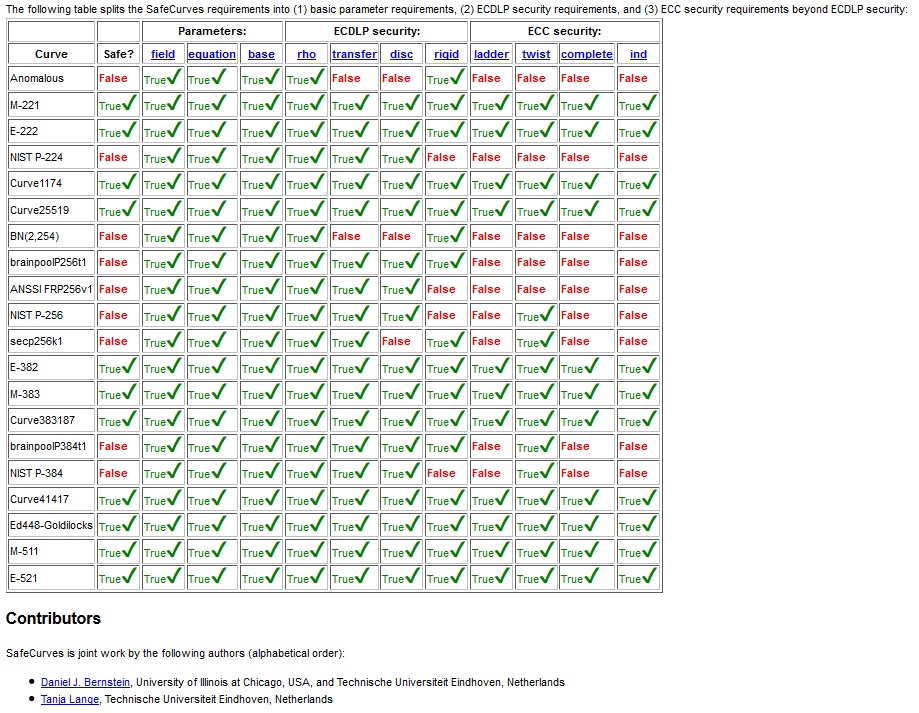
There is a fundamental problem with RSA and ECC encryption in most of the current browsers. Lately browsers prefer to support curves that are known to have vulnerabilities to manipulation as noted by the chart below as well. Insert all sort of conspiracy theories here!.
The EC secp521r1 was dropped by NIST and the NSA as the standard going forward. Microsoft and Chrome will still connect using our second choice secp384r1 in the config. The EC secp521r1 was dropped despite no warning about it being unsafe or there is a problem with the curve for security reasons. The EC secp521r1 is still widely used in EC implementations as noted by Microsoft. The chosen cipher secp521r1 is a bit slower I freely admit, but it has served me well for handling vast amounts of requests without any troubles in the most demanding of environments. If this is for a huge volume site with heavy processing power required for your application, I would suggest using whatever curve suits your needs.
These gentleman performed the following study: Daniel J. Bernstein and Tanja Lange. SafeCurves: choosing safe curves for elliptic-curve cryptography. http://safecurves.cr.yp.to/ Who says Academics do not have a sense of humor! https://SafeCurves.CR.YP.TO
HOWEVER they used a .to (Tonga) domain that is not DNSSEC TLD Signed or has a DS in root!!! Academics, sigh.
How does the Key Size make a difference?
We will use the secp521r1 curve since it is supported and hardly used. *** Notice that E-521 is considered to be secure*** This helps with lowering our risk of attacks a bit, but we trade a bit of performance for it. You can use any curve that the browsers support. Lets see how strong of Key and DH Parameter we need in order to achieve 100% for our test score and why. SSL Labs ratings are as follows:
Weak key (OpenSSL flaw) 0%
Anonymous key exchange (no authentication) 0%
Key or DH parameter strength < 512 bits 20%
Exportable key exchange (limited to 512 bits) 40%
Key or DH parameter strength < 1024 bits (e.g., 512) 40%
Key or DH parameter strength < 2048 bits (e.g., 1024) 80%
Key or DH parameter strength < 4096 bits (e.g., 2048) 90% <---Not Generating new DH Parameters will put us in this range
Key or DH parameter strength >= 4096 bits (e.g., 4096) 100% <---We will score here with an ECDH curve that is equivalent to 15360 bits RSA while incurring a tiny performance hit to do it!!!
- Straight RSA encryption under 2048 bit is not recommended
- Straight RSA encryption over 4096 bit and you lose Safari users
- Straight RSA encryption over 8192 and you lose most browsers support
- Apache is limited to straight RSA 8192 bit without questionable performance - Apache max is 16k bit & OpenSSL is 32K bit!
- Using Elliptical Curce Cartography (ECC) with Diffie-Helman will provide 7860 or 15360 bit eq. RSA without losing any browser support or performance!!!!