Identity Access Management
Defining Processes, Policies and Standards
Defining the detailed Policies and Processes
As organizations requirements and needs continues to evolve, organizations are required to adapt and refine their IAM (Identity and Access Management) governance practices. Crafting robust IAM standards, policies, and processes is a prerequisite for ensuring secure access control, underlining the need for consistent and effective security protocols.
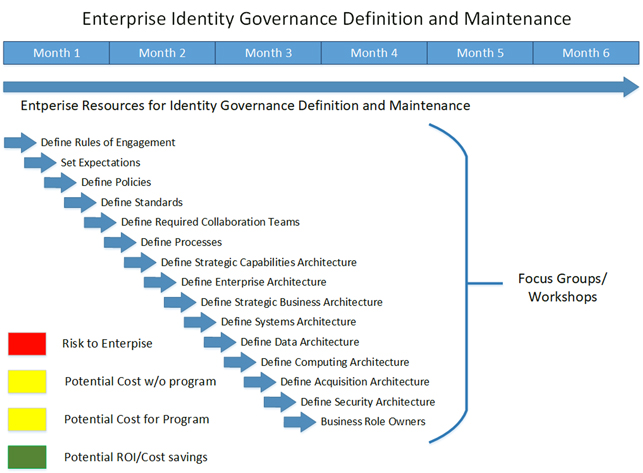
- Crafting Detailed IAM Policies and Processes:
- IAM Standards: The Foundation of Security:
- IAM Policies: Navigating Access Management:
- IAM Processes: Fine-Tuning Access Control Operations:
- Continuous Improvement: Embracing Change:
- Integration and Collaboration: Creating a Cohesive IAM Ecosystem:
- Set expectations for employees, contractors, students and other resources
- Clarity on who has what role
- Who reports to whom and what entitlements should be given
- Flexible to accommodate location, department and other differences without interrupting daily business operations
- Incorporate compliance concerns in standards
- Allow exceptions
- Justify the exception
- Out of norm for exceptions instead of the current status of commonplace
- Clarity on who has what role
The first step in defining IAM governance involves setting clear expectations for all users, including employees, contractors, and students. Policies should provide clarity on user roles, outlining who reports to whom, and what entitlements should accompany each role. Importantly, these policies need to be flexible, accommodating differences in location, department, and other variables, while avoiding disruption to daily business operations. Compliance concerns should be woven into the fabric of these standards, providing a framework for legal and ethical conduct. Exception handling is another crucial element. Policies should allow for exceptions when necessary, with a clear justification and under strict control, shifting the norm away from commonplace exceptions.
IAM standards act as the cornerstone of a robust security framework. They integrate industry-accepted best practices, state-of-the-art technologies, and stringent regulatory requirements. A case in point is the ISO/IEC 27001 standard, which provides a roadmap for establishing a rigorous information security management system (ISMS) encapsulating IAM aspects. Furthermore, industry guidelines such as the National Institute of Standards and Technology (NIST) Special Publication 800-53 offer an exhaustive list of security controls, inclusive of those associated with IAM. Adherence to these standards ensures alignment of an organization's IAM practices with industry norms, promoting the implementation of reliable access controls, identity verification procedures, authentication protocols, and data protection practices.
IAM policies serve as the compass for navigating access to organizational resources. These policies take into account a multitude of considerations, such as regulatory compliance, legal obligations, and sector-specific stipulations. In the healthcare sector, for instance, organizations must comply with regulations like the Health Insurance Portability and Accountability Act (HIPAA), which prescribes stringent access controls to safeguard sensitive patient data. IAM policies within such organizations must align with HIPAA stipulations, defining access controls, encryption standards, and privacy procedures specific to the healthcare industry. Likewise, different sectors may have distinct regulations and guidelines that shape IAM policies, such as the Payment Card Industry Data Security Standard (PCI DSS) for businesses handling card payments.
IAM processes fine-tune the orchestration of IAM-related activities. They cover various stages, from user onboarding and role-based access provisioning to access request and approval workflows, regular access audits, and offboarding procedures. Best practices and frameworks like the Information Technology Infrastructure Library (ITIL) offer valuable insights into process frameworks that organizations can incorporate into their IAM operations. The ITIL Service Transition process, for example, aids organizations in instituting robust change management procedures for executing IAM updates, facilitating seamless transitions with minimal business disruption.
It is imperative to understand that IAM standards, policies, and processes are not static constructs but dynamic entities that need to evolve with the changing landscape of threats, technologies, and regulations. Routine assessments, audits, and updates are indispensable for ensuring the effectiveness and relevance of IAM controls. Organizations must remain vigilant and informed about the ever-changing landscape of cybersecurity threats and compliance requirements, leveraging resources such as security communities, industry conferences, and threat intelligence feeds. A proactive and agile approach helps organizations respond swiftly to emerging threats while sustaining a robustsecurity posture.
An effective IAM strategy is one that is integrated and collaborative, mirroring the interconnectedness of the cybersecurity ecosystem. IAM standards, policies, and processes should harmonize with other industry norms, regulations, and internal stakeholders. For instance, a company operating within the European Union must comply with the General Data Protection Regulation (GDPR), which demands stringent data protection and access control measures. IAM policies and processes must, therefore, be aligned with the requirements of the GDPR, incorporating principles such as data minimization and purpose limitation.
Defining IAM standards, policies, and processes is a complex task that requires harmonization with industry standards, regulatory compliance, and a commitment to continuous improvement. By establishing robust IAM practices that integrate with existing frameworks, organizations can minimize risks, secure sensitive data, and ensure secure access control across their digital environment.
To summarize the goals: