Identity Access Management
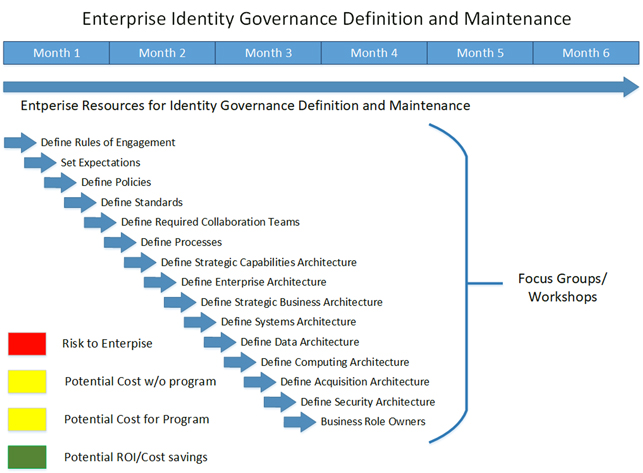
Building Robust Identity and Access Management (IAM) Governance: Process Definition
Defining the the Organizations Identity Governance Expectations
In today's rapidly evolving digital landscape, establishing robust governance processes, policies, and standards for Identity and Access Management (IAM) is crucial for organizations to protect their sensitive resources. By defining clear expectations and implementing effective controls, organizations can ensure that employees, contractors, students, and other resources have the appropriate access privileges, while maintaining flexibility to accommodate various factors without disrupting daily business operations. Let's delve into the key aspects of IAM governance and processes.
IAM Governance and Process Definition: Set expectations for employees, contractors, students, and other resources
Clarity on Roles and Responsibilitie:
A fundamental aspect of IAM governance is providing clarity on who has what role within the organization. This entails a clear identification of roles and responsibilities, ensuring that each individual's reporting structure and entitlements are well-defined. By establishing a comprehensive understanding of the roles within the organization, it becomes easier to assign appropriate access privileges and ensure accountability.
- Clear identification of roles and responsibilities
- Reporting structure and entitlements
Least privilege access is a fundamental principle in the realm of cybersecurity, ensuring that users are granted only the minimum privileges necessary to perform their specific job functions. By implementing least privilege access, organizations create a robust security environment where users are restricted to the domain of privileges essential for their tasks, without unnecessary access to sensitive resources. This principle involves a meticulous process of identifying each user's job role, thoroughly assessing the exact set of privileges required for their responsibilities, and meticulously tailoring their access rights accordingly. With the principle of least privilege in place, organizations can effectively minimize the potential attack surface, mitigate the risks of unauthorized access or data breaches, and safeguard the integrity and confidentiality of their critical assets.
Flexibility for Business Operations
IAM governance processes should be designed to accommodate the diverse requirements stemming from differences in location, departments, and other factors, while still maintaining effective security controls. Flexibility is essential to support the dynamic nature of business operations, enabling organizations to adapt to changing circumstances without compromising security. This includes implementing mechanisms that allow for seamless onboarding and offboarding of users, granting access based on specific business needs.
Incorporating Compliance Concerns
Aligning IAM policies and standards with compliance requirements and regulations is paramount for organizations. By incorporating compliance concerns into IAM governance, organizations can ensure that access controls adhere to industry best practices and legal obligations. This involves continuously monitoring and updating policies to stay in line with changing regulatory landscapes, safeguarding against potential risks and vulnerabilities.
Allowing Exceptions with Justification
While IAM policies should provide a comprehensive framework for access management, it is important to allow exceptions in certain cases. However, exceptions should be carefully evaluated and justified on a case-by-case basis. Organizations should establish clear processes for requesting exceptions, ensuring that valid justifications are provided and assessed thoroughly. Exceptions should be treated as deviations from the norm and should not become common practice, maintaining the integrity of the IAM program.
Policies: The Backbone of Cybersecurity
IAM policies form the backbone of a cybersecurity program, dictating the rules, standards, and guidelines for accessing and using organizational resources. Well-crafted policies establish a framework that enforces security measures, defines acceptable use, and regulates data handling practices. These policies should align with industry best practices and legal requirements, empowering organizations to consistently enforce security controls and effectively respond to emerging threats. Regular reviews and updates should be conducted to ensure policy relevance in the face of evolving risks
Real-Time Reporting for Insightful Analysis
The ability to generate comprehensive and real-time reports is a critical aspect of IAM governance. Reporting capabilities allow organizations to monitor and assess the effectiveness of their cybersecurity measures. Through detailed insights into user activity, access patterns, and potential security incidents, organizations can proactively identify anomalies, address policy violations, and detect potential breaches. Real-time reporting empowers organizations to respond promptly and mitigate security risks, reinforcing the overall effectiveness of the IAM program.
Risk-Based Determination for Optimal Access Control
Integrating risk-based determination into IAM governance processes enables organizations to dynamically adjust access controls based on risk profiles. By assessing contextual factors such as user roles, sensitivity of data, and external threats, organizations can determine the appropriate level of access and security controls. This adaptive approach enhances the effectiveness of the cybersecurity program, ensuring that resources are adequately protected without impeding productivity.
Self-Service Empowerment
Self-service features play a vital role in IAM governance, empowering users to manage their own access privileges within predefined boundaries. By providing self-service capabilities, organizations can streamline access request and approval processes, reducing administrative burden and enhancing user satisfaction. Well-designed self-service mechanisms integrate seamlessly with identity governance and administration systems, ensuring that user actions are compliant with established policies and protocols.
Continuous Monitoring for Timely Threat Detection
Continuous monitoring is a cornerstone of effective IAM governance. Robust monitoring solutions provide real-time visibility into network traffic, user behavior, and system logs, enabling the identification of potential threats or vulnerabilities. By continuously monitoring access activities, organizations can detect security incidents in a timely manner, facilitating prompt response and minimizing the potential impact. Monitoring supports ongoing improvements in security controls, ensuring the IAM program remains robust and adaptive.
Harnessing Real-Time Analytics
Integration of real-time analytics within the IAM governance framework empowers organizations to detect anomalies, patterns, and emerging threats promptly. By leveraging machine learning algorithms and AI technologies, organizations can proactively identify and respond to security incidents in real-time. Real-time analytics enable swift and accurate decision-making, strengthening the overall security posture of the organization.
Persistence for Long-Term Security
Persistence refers to the consistency and durability of security measures throughout the organization. It ensures that cybersecurity practices are not dependent on individual personnel or system updates. A persistent cybersecurity program establishes a culture of security awareness, ongoing training, and regular evaluation and adaptation to evolving threats. This long-term commitment bolsters the resilience and effectiveness of the IAM program.
IAM governance and processes provide the foundation for a secure access control framework within organizations. By integrating clear roles and responsibilities, flexibility, compliance considerations, exceptions management, well-crafted policies, real-time reporting, risk-based determination, self-service empowerment, continuous monitoring, real-time analytics, and persistence, organizations can build a comprehensive IAM program. This program aligns with business objectives, safeguards sensitive information, and mitigates the ever-evolving risks of cyber threats. IAM governance ensures that security remains a top priority, fostering a culture of security throughout the organization.