Identity Access Management
Creating/Improving an Enterprise Identity Access Management Program
In the realm of cybersecurity, protecting secrets and sensitive information is of utmost importance. Just as historical figures relied on trusted individuals and physical security measures to safeguard their secrets, modern organizations employ Identity and Access Management (IAM) to protect identities, maintain confidentiality, and mitigate cyber threats. Let's explore the historical context, the relevance of IAM in today's digital age, and the crucial role of identity protection from a cybersecurity perspective.
Throughout history, the safeguarding of secrets relied on trusted individuals and physical security measures. Kings and queens entrusted loyal guards and advisors who were carefully selected based on their trustworthiness, loyalty, and dedication. These individuals were bound by oaths of secrecy and were fully aware of the severe consequences of betraying that trust. The measures taken in those times helped maintain confidentiality and protect sensitive information. While the loss or inappropriate sharing of secrets had its consequences, the effects were not always immediate or profound. In the modern digital age, however, the accuracy and impact of losing secrets are immediate and far-reaching.
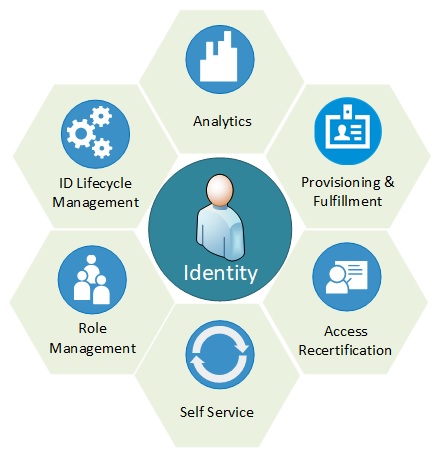
As we transitioned into the digital age, protecting identities and secrets necessitated a combination of technical measures and human factors. IAM emerged as a comprehensive framework that empowers organizations to establish policies, implement security controls, and train employees to handle and protect confidential information. IAM's multifaceted approach encompasses various aspects of identity and data protection in the digital age.
User authentication serves as the foundation of IAM. Robust mechanisms such as biometrics and multi-factor authentication verify the identities of individuals accessing systems or services, preventing unauthorized users from gaining access to sensitive data or resources. Passwords, which were once a common method of authentication, now have become a threat to organizations. IAM enables organizations to define a person's identity in relation to the organization and their role within it.
IAM serves as an essential component of modern cybersecurity strategies, enabling organizations to protect identities, maintain confidentiality, and mitigate cyber threats. By embracing the best practice IAM principles and practices, organizations can safeguard sensitive information, prevent unauthorized access, and establish a secure and trustworthy digital environment for their workforce, customers, members, distributors, suppliers, and products.
Where to begin or how to improve an existing architecture?
To begin or alter an existing architecture for creating the best practices Identity Access Management (IAM) program, the following steps can be taken:
- Assess Current State:
- Define Program Goals:
- Establish Performance Measurement Framework:
- Identify Key Performance Indicators (KPIs):
- Implement Monitoring and Reporting Mechanisms:
- Continuously Improve:
- Communication and Stakeholder Engagement:
Evaluate the existing IAM program to understand its strengths and weaknesses. Identify areas that need improvement and determine the gaps between the current state and the desired state.
Clearly articulate the goals of the IAM program based on the specific needs and requirements of the enterprise. These goals should align with the overall mission of the organization and the critical success factors of IAM.
Develop a framework for measuring the outcomes and effectiveness of the IAM program. This framework should include performance indicators that address the primary characteristics of effective performance measurement, namely relevance, understandability, comparability, timeliness, consistency, and reliability.
Select KPIs that align with the program goals and reflect the desired outcomes. For example, KPIs could include metrics related to identity data accuracy, access management effectiveness, governance compliance, and user satisfaction.
Put in place mechanisms to monitor and track the selected KPIs on an ongoing basis. This may involve leveraging IAM tools and systems that provide real-time or near real-time updates. The monitoring and reporting mechanisms should be designed to ensure data accuracy, timeliness, and consistency.
Regularly review the performance measurement data and analyze the trends and patterns. Use this information to identify areas for improvement and make informed decisions to enhance the effectiveness of the IAM program. Continuously refine the architecture and processes based on the insights gained from the performance measurement data.
Communicate the program goals, performance measurement framework, and progress to relevant stakeholders, including program participants and senior management. Engage stakeholders throughout the process to build enthusiasm and ensure alignment with the overall mission.
By following these steps, an organization can establish a strong foundation for an effective IAM program that focuses on measurable outcomes and continuous improvement. It is important to regularly revisit and update the architecture based on evolving business needs, technology advancements, and regulatory requirements to ensure the IAM program remains relevant and effective over time.
Use your Program Goals to define a clear vision and build enthusiasm among the program participants. Set your Program Goals to support the mission.