Identity Access Management
Next Steps for Identity Management, Access and Governance?
Where do we go from here?
Do you need more help with rolling this very topic for your organization? We are here to help! Organizations are working on complying with laws, while developing tighter security controls within limited budgets. Being able to react to market changes and trends is vital to remaining competitive in today’s market. Understanding how to leverage the technology investments being made today while providing future value to the organization;
What can Zombie Security offer your organization....just ask and we will post it for you?
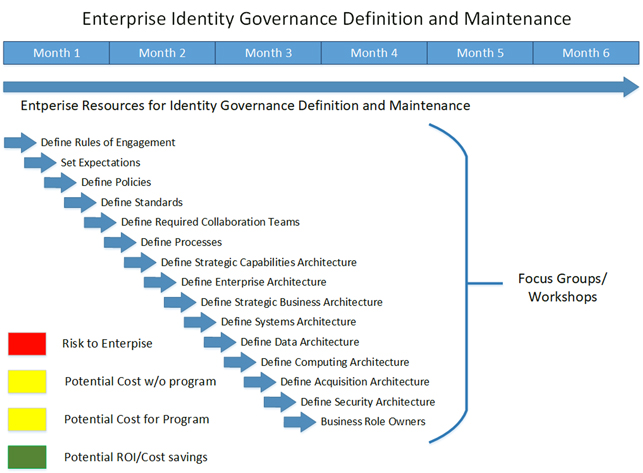
- ) Identity Management (IDM) Workshops
- ) Identity Access Management (IAM) Workshops
- ) Identity Governance (IG) Workshops
- ) Technical resources for Architecture, Design, Implementation and Maintenance
- ) Program Management for Identity, Access and Governance
- ) Security Program Management
- ) Technical resources for Identity Architecture, Design, Implementation and Maintenance
- ) Technical resources for Security Architecture, Design, Implementation and Maintenance
- ) Organizational Assessment
- ) Vendor recommendations based on your organizations requirements
Basic example assessment:
- Review current organizational policies, governance and compliance standards
- Understand the market and competitive landscape
- Understand the organization overall status within the framework
- GAP analysis of current state versus optimal state
- Determine the prioritization of any remediation required to current status
- Determine budget and hierarchy of initiatives for Road Map
- Disaster Recovery requirements and remediation
- Brainstorm, review, or create measures for new products and emerging technologies
- Determine what products, technologies and resources will fulfill the organizational needs today and tomorrow
- Determine significant systems strategy and handling of sensitive data
- Review, recommend and explain steps for continuing a fluid and dynamic service-oriented architecture
- Differing business units, locations and employee populations requirements
- Review current identity model architecture and all associated applications
- Plan, review and assess projects for lifecycle capabilities within the organization
- Products, policies, procurement and potential risk
- Review resources for current and long-term strategies
- Review Mergers and Acquisitions (M&A) strategies’ for on/off-boarding organizations
- Determine best practice methodologies and architectures for minimal impact with organizational on/off boarding