SSO, MFA & PAM Documentation
What is Multi-Factor Authentication (MFA)? What are the Benefits and Goals?
Multi-Factor Authentication (MFA)
What is it and what does it do?
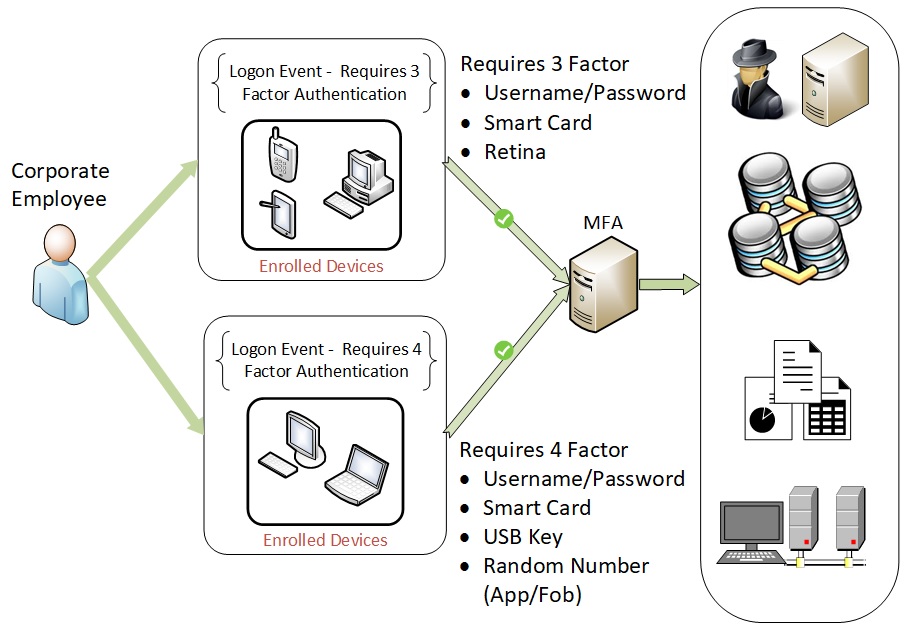
Multi-Factor Authentication (MFA) is a security mechanism for verifying a user’s identity by requiring multiple authentication methods. Basic authentication, traditionally is a username and password. Instead, MFA requires additional methods to verify you are who you say you are. These methods may include a code from a smart phone, answering security question, facial recognition and so forth.
MFA is an effective way to provide enhanced security and confidence for log in. Traditional username/password combination can be easily lost or hacked. MFA creates multiple layers of security to help increase the confidence the user requesting access is actually who they claim to be. We explore this topic in depth in a later section.
Organizational Benefits
- Comply with all applicable Laws and Regulations pursuant to the business. (PCI, SOX, FERPA, etc)
- Comply with all applicable Standards pursuant to the business (NIST, ISO, ITIL, DevOps,etc.)
- Minimize access to resources only needed for Job Role
- Higher security standards by using Multi-Factor Authentication based on log in policies and location
- Multi-purpose use for controlling location, area, room access when used with RFID devices
- Lower costs - Less escort personnel when Geo-Fencing is deployed by Wireless, Bluetooth, Cellular, or Global Positioning Systems (GPS) within ID Badges or RFID Devices
- Header Injection for certain ID Profile Attributes to share with other systems or resources..
- Step-Up Authentication or Multi-Factor Authentication (MFA) - Based on policies
- Analytics and reporting in real-time for access issues
- Bring Your Own Device (BYOD)
Goals of Multi-Factor Authentication (MFA)
- We want to use MFA to ensure the utmost confidence the right person is logging in to enterprise resources
- Have policies that determine the number/type of authentication methods based on access level/data sensitivity
- Have policies that determine the number/type of authentication methods based on access location
- Have policies that determine the number/type of authentication methods based on risk
Accomplished by using software that integrates with the enterprise Identity store(s) and provides the desired Authentication Methods & Geo-Fencing