SSO, MFA & PAM Documentation
Best Practices for Privileged Access Management (PAM)
What is Privileged Access Management (PAM)?
A privileged user/account has administrative or privileged access to mission critical enterprise systems These critical systems have high risk associated with them to the organization. Privileged users can be employees or contractors, remote or local, human or automated accounts for their use. These accounts may include root, administrator, service and numerous other accounts which we desire to control access. An example, anyone who can access a database in a Human Resources (HR) system is a privileged user. This privileged user might see Personally Identifiable Information (PII) if the database is not encrypted properly.
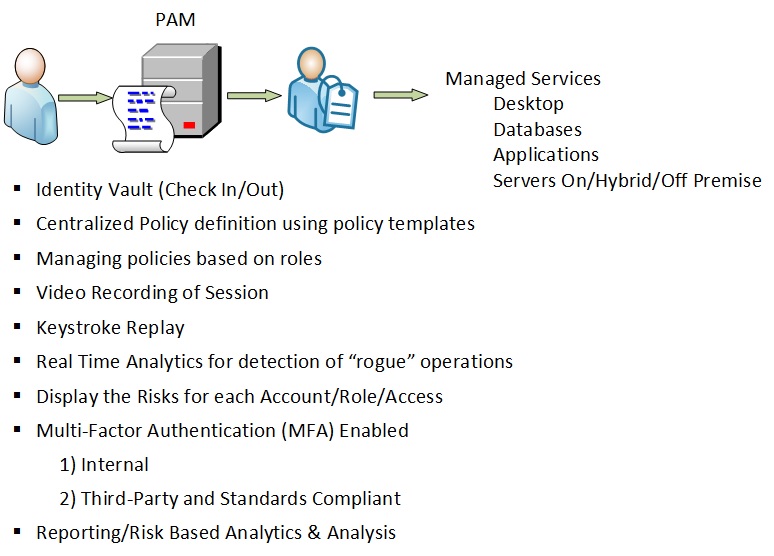
PAM offers a scalable and secure way to authorize and monitor all privileged accounts across all your systems. PAM allows you to:
- Grant privileges to users only for systems on which they are authorized.
- Grant access only when it’s needed and revoke access as soon as the need expires.
- Eliminate local/direct system passwords for privileged users.
- Centrally manage access over a disparate set of heterogeneous systems.
- Create an unalterable audit trail for any privileged operation.
A privileged account should only be extended to trusted people within your organization. The scary reality of exploiting privileged accounts, as noted by Forbes, is a very real reality in every organization.
Many organizations have more privileged users than employees!
The result is an explosion of growth for the “Privileged Access Management” software sector. According to Gartner, this sector is growing quickly around the world.
You give accounts with elevated privileges to those key organizational assets that you trust. This is where is the “trust but verify” position for making PAM a justifiable case within any organization. We trust you but we still desire to have levels of control and monitoring to ensure there are no rogue actions being taken. Yes, even trusted people with privileged access need to have policies in place, limitations on actions while being monitored.
The best practice is to limit privileges to those who need them, when they need them and then return them after the task is performed.