Single Sign-On (SSO) Certificates
What is Secure Sockets Layer (SSL) & Transport Layer Security (TLS) - How does it help to protect Web communications?
What is the difference between Public and Private Key Infrastructures (PKI)?
Public Key Infrastructure
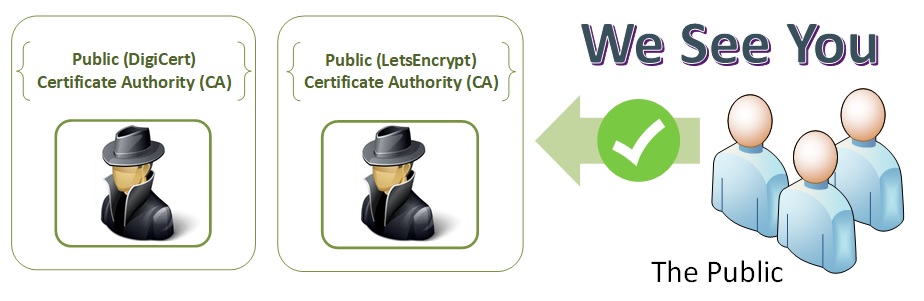
A Public Key Infrastructure is the public distribution, revocation and verification of public keys used for public key encryption exchange. The CA's Public Key Infrastructure enables linking and verifying the validity of the identities with public key certificates. This process is verifying the legitimacy of certificate holders such as web servers, email, authenticate servers and individuals to the actual identity in the certificate. This provides a level of trust deemed acceptable for users and systems to securely exchange data over the internet.
Private Key Infrastructure
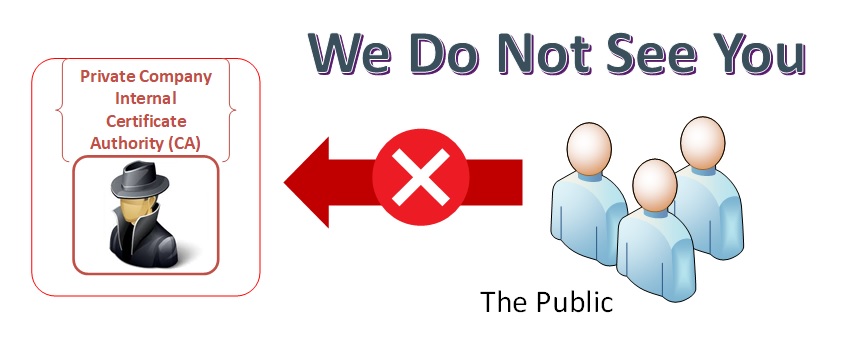
It is essentially the same and a Public Key Infrastructure, but it is not meant for secure communications within the public space. The public CA's have their root certificates within the all of the internet browsers and then check a public revocation list to ensure the certificate or CA is still valid. If you were to visit a company web site with an internal certificate, it would appear as "insecure" to the browser and give you a warning. If you were an employee with the root certificate in your company browser, it would appear as a normal web site. Private Key infrastructures are used to limit the people who can interact with corporate assets.
The "Key" for SSL/TLS communications
To use SSL/TLS (Secure Connection) you need to provide a set of public/private keys. The TLS\SSL KeyStore contains a private key that is used to prove the authenticity of this SSL/TLS side to the other side of an SSL/TLS connection. The SSL/TLS trust store contains public key certificates of trusted parties.
To setup keys for your server, you can:
Option 1 - Generate a private key and a corresponding self-signed public key certificate and put it in your KeyStore. (Self Signed)
Option 2 - Obtain a certificate from a Certificate Authority and replace your self-signed certificate with it. (Private/Public Certificate Authority)
Option 3 - Export the public key certificate of your secret key and distribute it to the parties that will interact with you. (Client Authentication required - Employees are issued personal certificates)
SSL IS DEAD!!!
Yes, it was the first iteration of secure communications but it is not safe to use anymore. It takes less than a couple of minutes at most to hack any version of SSL. We will use the SSL term going forward since it is common to refer to secure communications.
- ) SSL Version 1, 2 3 Do not use for any reason!!!
TLS is the new standard
As the National Institute of Standards and Technology (NIST) notes - Sensitive data—from credit card numbers to patient health information to social networking details—need protection when transmitted across an insecure network, so administrators employ protocols that reduce the risk of that data being intercepted and used maliciously. TLS, a standard specified by the Internet Engineering Task Force, defines the method by which client and server computers establish a secure connection with one another to protect data that is passed back and forth. TLS is used by a wide variety of everyday applications, including email, secure web browsing, instant messaging and voice-over-IP (VOIP).
- ) TLS Version 1 and 1.1 - Do not use - Yes, we even kick TLSv1.1 to the curb. It is used by very few applications.
- ) TLS Version 1.2 - Current standard
- ) TLS Version 1.3 - should be used with caution until the standards are solidified