Single Sign-On (SSO) Certificates
What is Certificate Chaining for a public web site?
How does a Public Key Infrastructures (PKI) work for web sites?
The "Key" for SSL/TLS communications
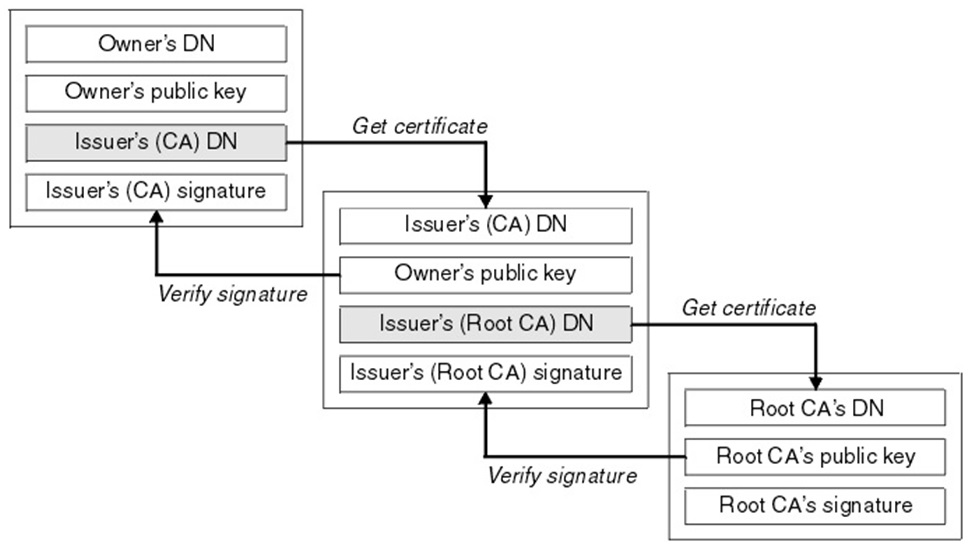
As noted by Thawte - A certificate chain is an ordered list of certificates, containing an SSL/TLS Certificate and Certificate Authority (CA) Certificates, that enable the receiver to verify that the sender and all CA's are trustworthy. The chain or path begins with the SSL certificate, and each certificate in the chain is signed by the entity identified by the next certificate in the chain.
Any certificate that sits between the SSL Certificate and the Root Certificate is called a chain or Intermediate Certificate. The Intermediate Certificate is the signer/issuer of the SSL Certificate. The Root CA Certificate is the signer/issuer of the Intermediate Certificate. If the Intermediate Certificate is not installed on the server (where the SSL certificate is installed) it may prevent some browsers, mobile devices, applications, etc. from trusting the SSL certificate. In order to make the SSL certificate compatible with all clients, it is necessary that the Intermediate Certificate be installed.
What makes up the Chain of Trust for a web site
The process involves our generated Private Key being used to decrpyt the Public Key contained within the our sites certificate. We also need to have the CA who verified (Signed) or our certificate Public Keys (Root and Intermediary Certificates) to create the chain of trust.
- ) Valid web site (zombiesecured)
- ) Check certificates to determine validility
- ) Certificate Chaining
- Certificate Authority (CA)
- Intermediate Certificate
- Zombiesecured.com Ceritifcate
- ) Your trust of the CA Root certificate, Intermediate certificate(s), Web site certificate(s) and Hyper Text Transfer Protocol Secure (HTTPS)

How to create a Chain of Trust for a web site
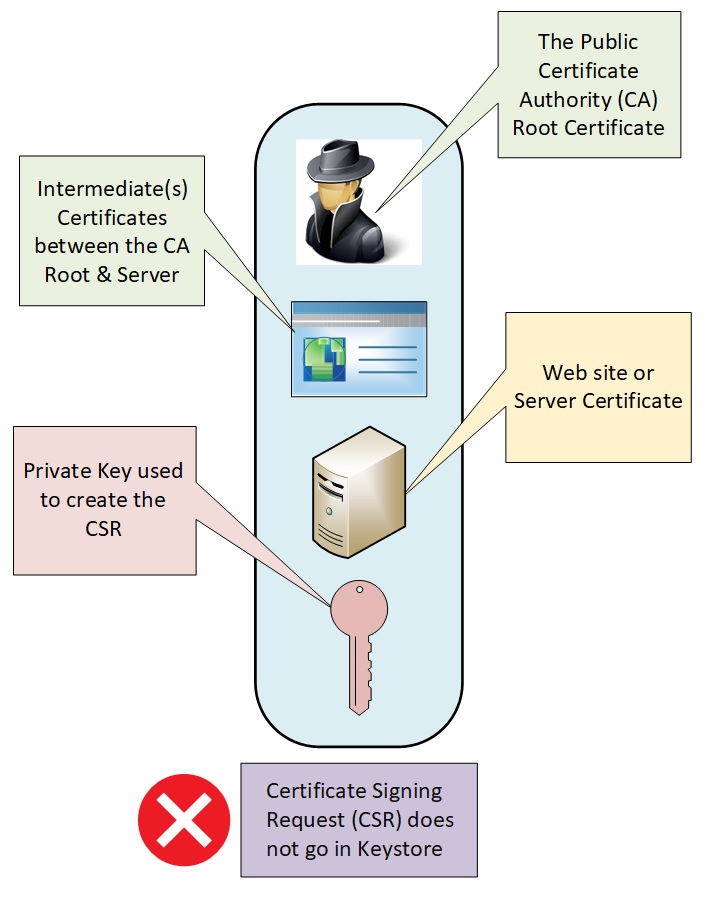
The procedures on how to create the Key, Keystore and Certificate Signing Request (CSR) are in the examples and tutorial sections of this site.
- ) Create Private Key and KeyStore
- ) Create Certificate Signing Request (CSR)
- ) Send CSR to Certificate Authority (CA)
- ) Certificate Authority returns Signed Certificate
- ) Install Certificate Chain from CA - Root & Intermediate certificate(s)
- ) Install the Signed Certifcate from the CA